Migration from PSA to ISA
On the existing PSA platform. Log in to the standalone device or the primary node of the cluster (where the cluster was first formed) and export its binary configs (system.cfg and user.cfg), and the XML Network settings configurations.
Refer to Prerequisites for Migration and Supported Configuration Migration Path before starting the migration.
Migration procedure explained in this document applies to both ISA and ISA-V Gateway.
Exporting Configurations
To export the binary configurations from the PSA Gateway:
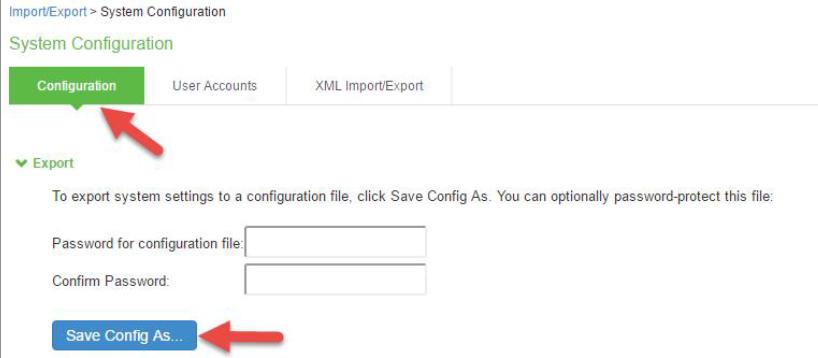
1.From the PSA Gateway Admin UI, select Maintenance > Import/Export > Configuration.
2.Under Export, enter a password if you’d like to password-protect the configuration file.
3.Click Save Config As to save the file. The default filename is system.cfg.
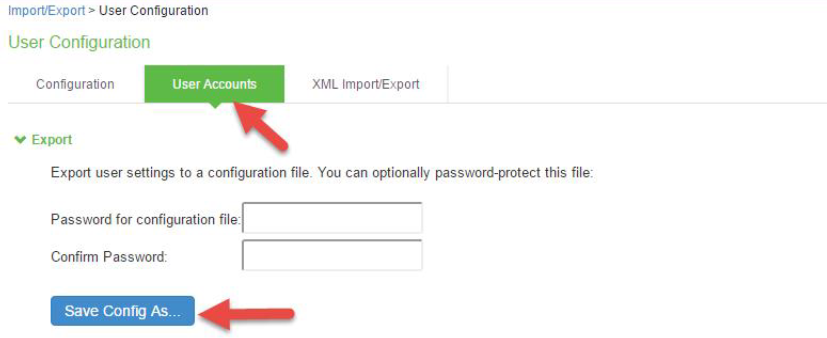
4.Select Maintenance > Import/Export > User Accounts.
5.Under Export, enter a password if you’d like to password-protect the configuration file.
6.Click Save Config As to save the file. The default filename is users.cfg.
To export the XML Network configuration:
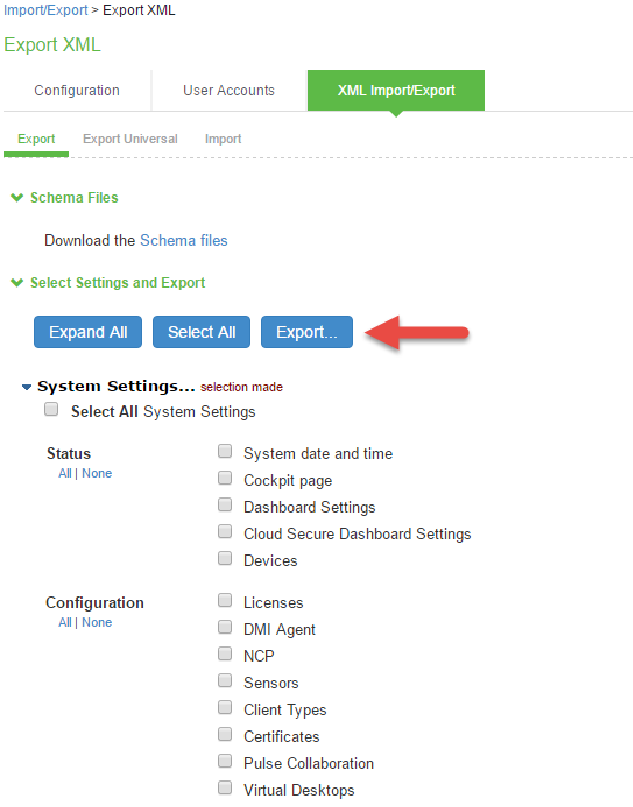
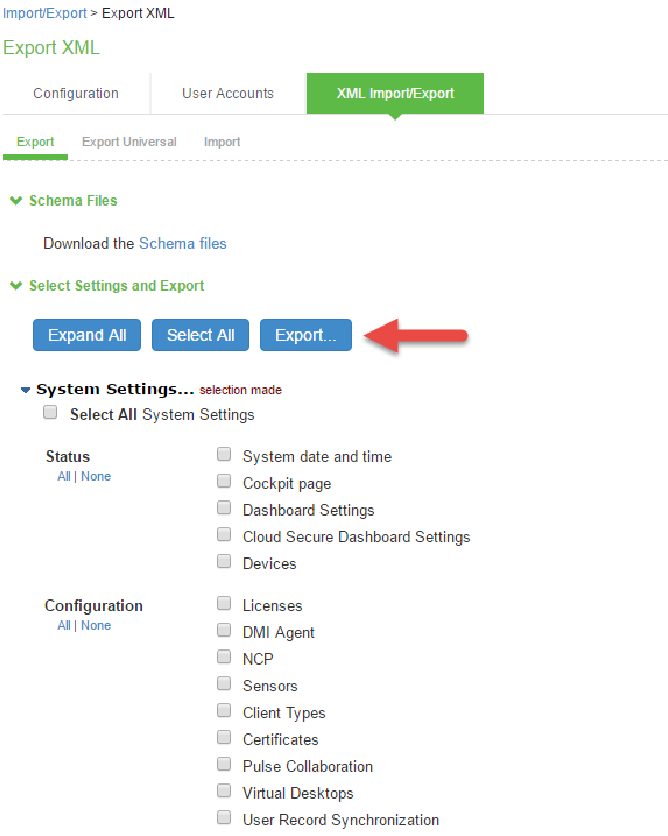
1.Select Maintenance > Import/Export > XML Import/Export.
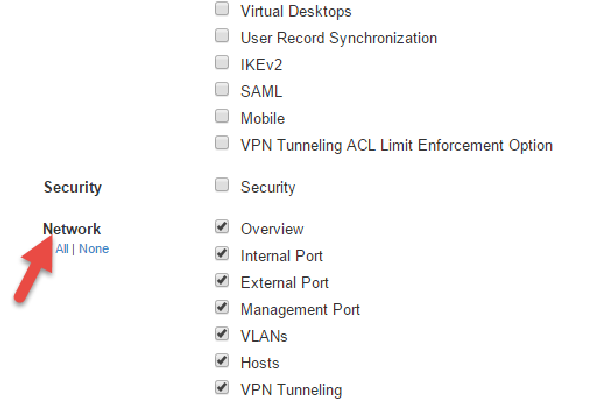
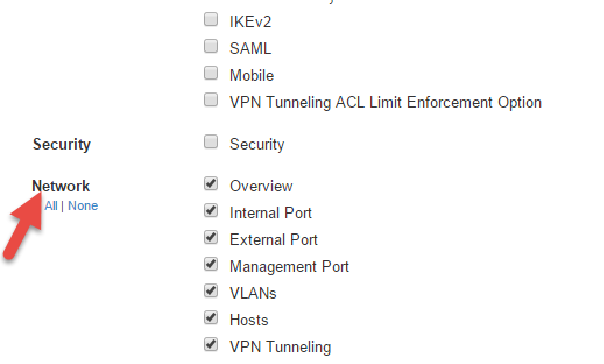
2.Under Export, expand System Settings and select Network > All.
3.Click Export and save the XML file.
Active Directory Legacy Mode configuration is not supported. If you have an existing Active Directory authentication server using Legacy Mode, first migrate to Standard Mode and then upgrade CS. For the detailed AD migration procedure, refer KB40430.
Make notes of all the local settings for both nodes (if not yet done during preparation stage): IP information, clustering, virtual ports, VLANs, hosts, routes, DNS settings, SNMP (if configured), Syslog.
Ivanti recommends using standalone nodes or clusters of a maximum of 2 nodes behind a load balancer.
Ivanti Security Appliance (ISA) does not support clusters containing more than two nodes for ICS.
Configuring ISA
1.Configure the new ISA devices with same internal/external/management ports IPs with same IP addresses as the old PSA devices and the proper DNS settings. Do not configure any other settings at this point time.
2.Apply the proper licenses for the new ISA devices. If the PSA device is a member of an Enterprise License Server, you must manually recreate the client and re-establish connection to the license server later at the end of migration.
If you are upgrading a non-clustered PSA device, skip next 4 steps and proceed to Step 7.
3.In the new ISA device (first device), manually create a new cluster with same name and settings with same node names as the old PSA cluster.
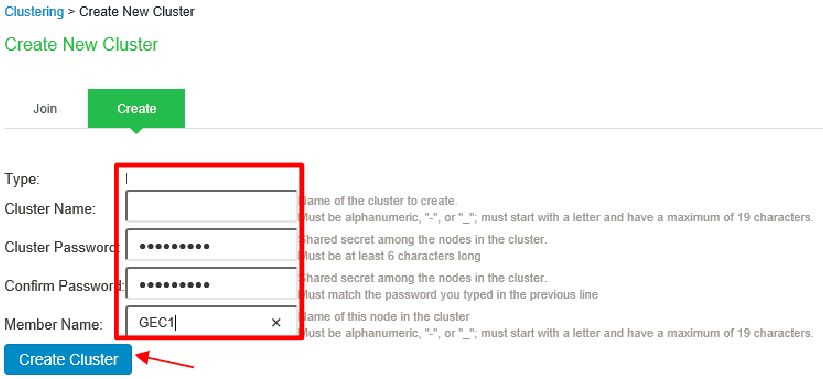
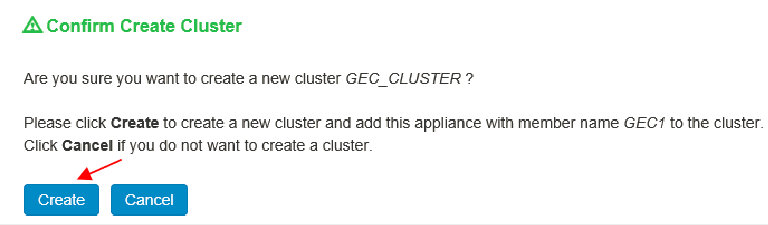
4.Add the second device to the cluster in the primary node cluster configuration and save the settings.
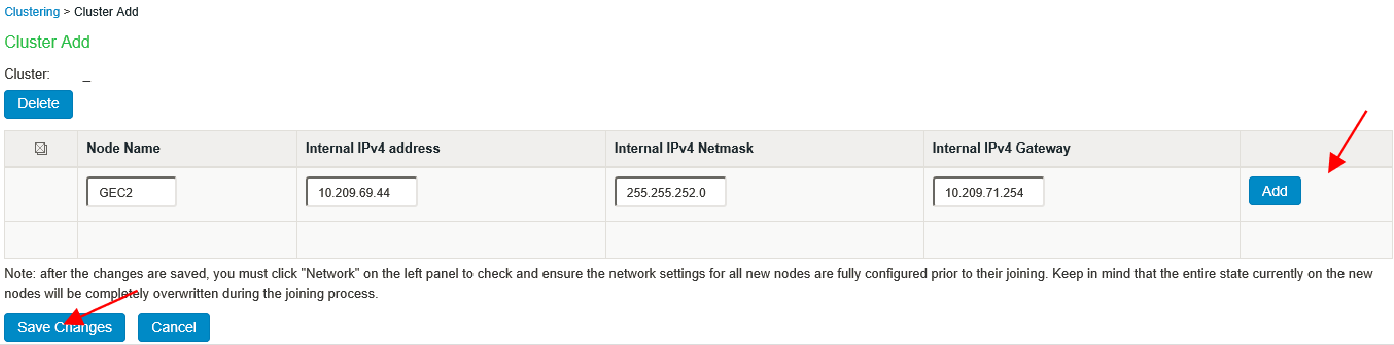
a. Click Add Members to add a member.
b. Enter member node name and IP and check netmask and gateway, then click Add.
c. Click Save Changes.
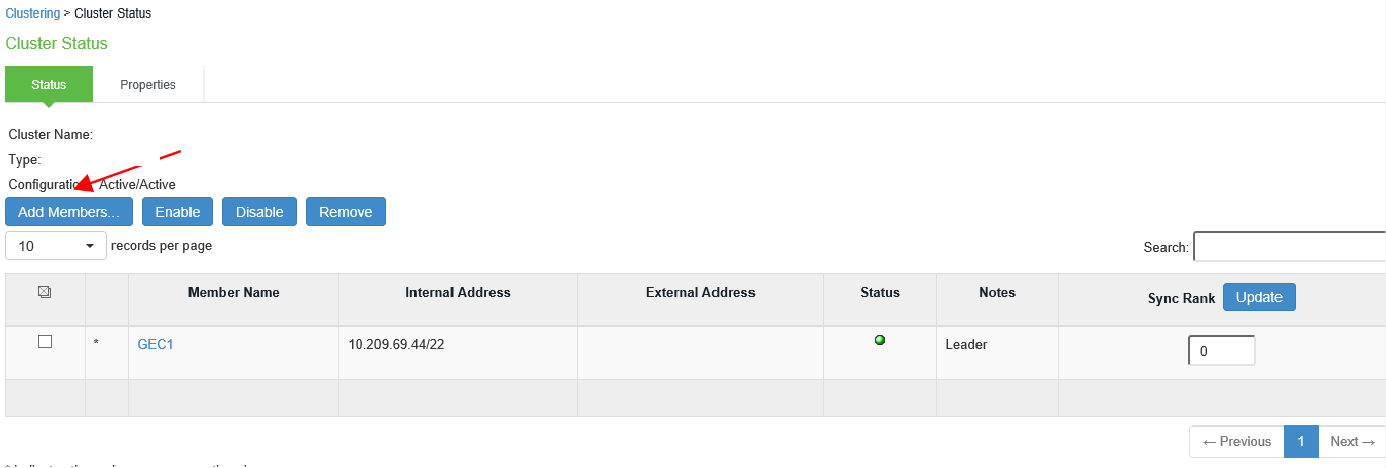
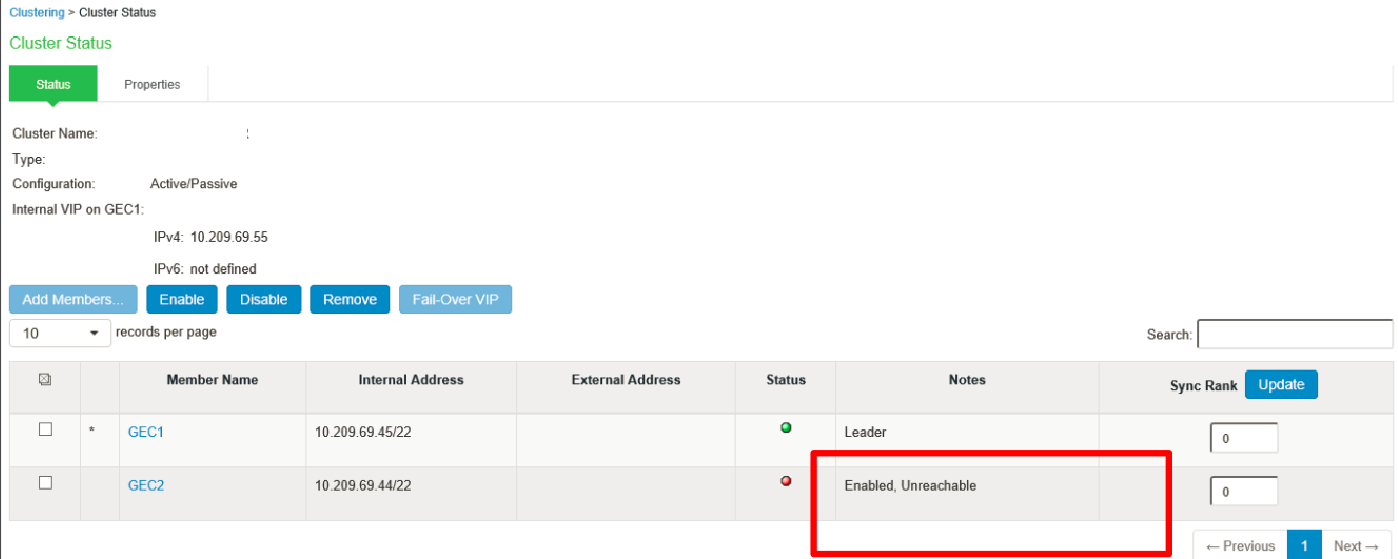
d. Check cluster status.
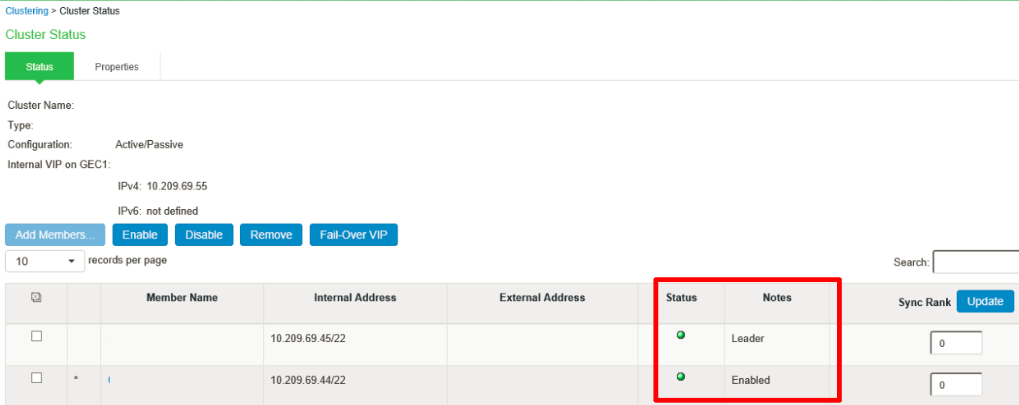
The status turns transitioning for short period, then the first node becomes enabled, and the status turns as Leader. The second node remains Enabled, Unreachable until it joins the cluster.
5.If the XML config is exported from an Active/Passive Cluster, following needs to be done prior to XML Import:
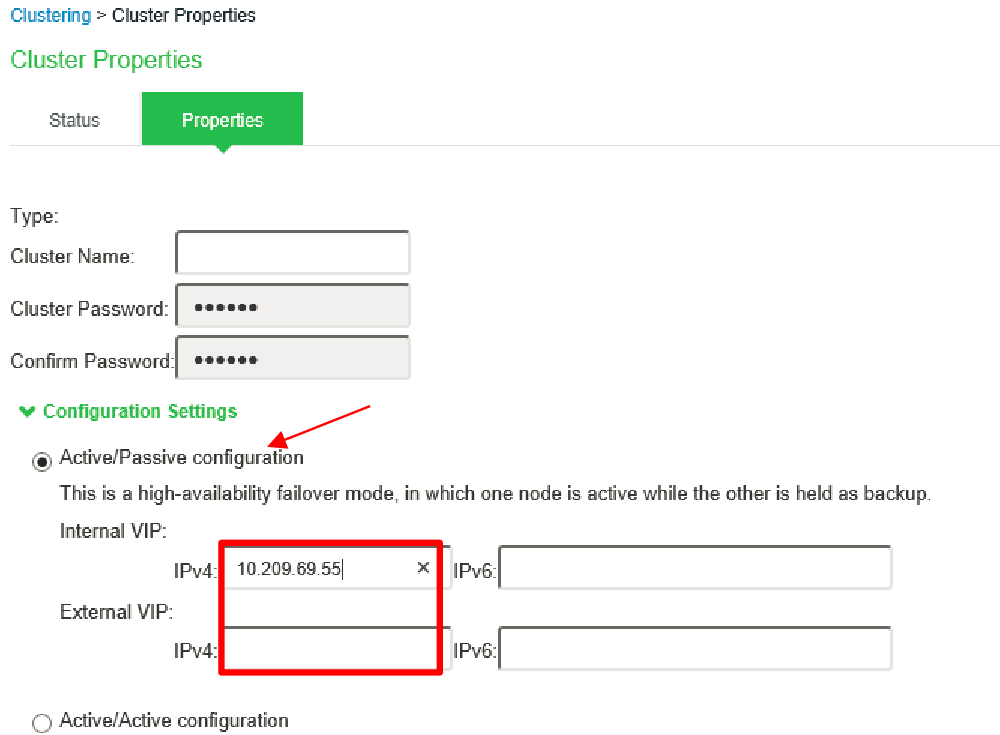
a. Configure External Port for the Cluster Members (if external ports are configured in cluster).
b. Go to Clustering > Cluster Properties page. Change the Cluster Type from Active/Active to Active/Passive and add the cluster VIP address/es (the example here does not use external port
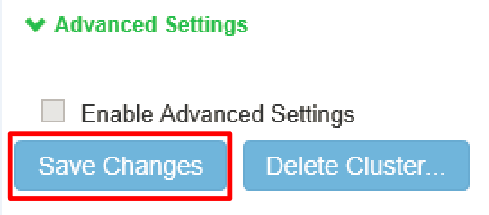
c. Save the cluster configuration settings.
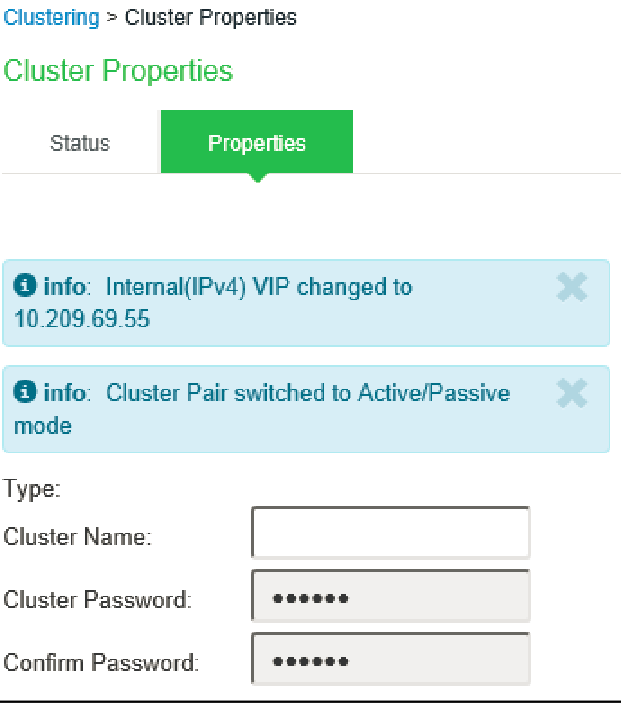
d. Change confirmation will appear confirming change from Active/Active to Active/Passive.
e. Log in to the second PSA device and join this node to the cluster by Clustering > Join Cluster.
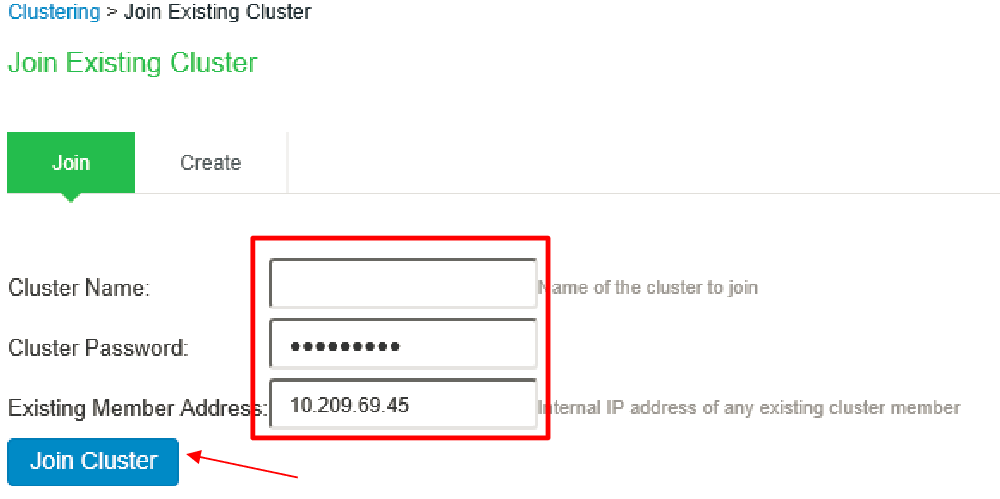
f. Click Join.
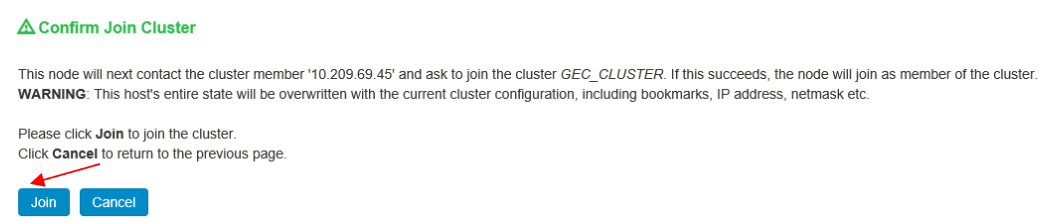
6.Log in to primary node and check cluster status and it should stabilize in a few minutes.
7.In the standalone environment or primary node of the new cluster, do the XML Import of Networking Settings. All networking settings would get imported, including the following:
•Internal Virtual Ports
•External Virtual Ports
•Management Ports
•VLANs
•Static Routes
•Port settings
8.In the standalone environment or primary node of the new cluster, import the system.cfg (this is the same process in a standalone mode migrate).
Importing existing PSA configurations to ISA
To import the configurations to ISA Gateway:
1.From the ISA Gateway Admin UI, select Maintenance > Import/Export > Configuration.
2.Select Import Everything except network settings, cluster settings, and licenses to import all configurations except network, cluster and license settings.
3.Browse to the configuration file, system.cfg. Enter the password if specified.
4.Click Import Config.
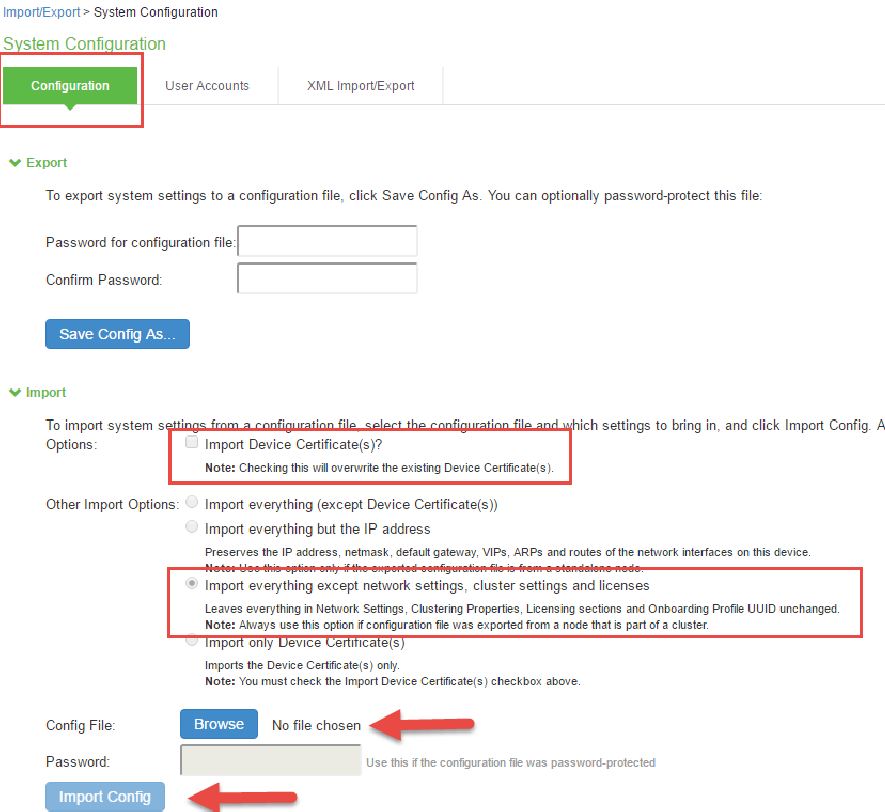
When importing the PSA configurations to ISA all the system configurations will be imported. (Configurations related to ICS deprecated features, and IPS deprecated features will be removed).
5.Select Maintenance > Import/Export > User Accounts and browse to the users.cfg file.
6.Click Import Config.
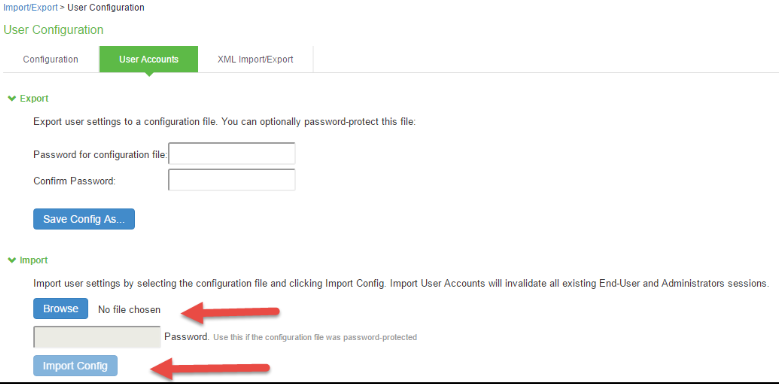
When importing the PSA configurations to ISA all the user configurations user configs like realms, sign-in policies, host checker, policies, roles, devices, users will be imported. (Configurations related to ICS deprecated features, and IPS deprecated features, will be removed).
7.For XML import, select Maintenance > Import/Export > XML Import/Export and import the config file. After importing XML, system and user.cfg files, check and/or modify/add remaining local settings and other settings such as:
a. System > Network > Overview settings (set in cluster or individual nodes).
b. System > Network > Routes (for internal, external and other ports).
c. System > Network > Hosts (set in cluster or individual nodes).
d. System > Network > Internal Port/ External Port>Virtual Ports (if clustered, set this up in cluster “Entire Cluster”).
f. System > Network > VLANs (if clustered, set this up in cluster “Entire Cluster”).
e. ICS only- System > Network > VPN Tunneling (set in cluster or individual nodes).
g. System > Log/Monitoring > SNMP (set in cluster or individual nodes).
h. System > Configuration > Certificates > Device Certificates (and its ports bindings).
f. ICS only - Users > Resource Policies > VPN Tunneling > Connection Profiles (if configured).
k. System > Configuration > Licensing - License client-server settings (if used as license client in Enterprise Licensing Server environment), proper licenses installed.
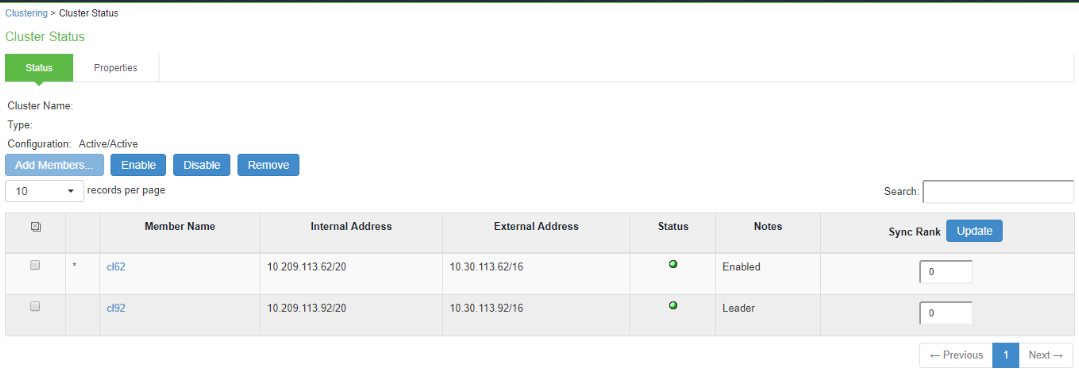
8.Check cluster status (if clustered) and test operation by logging in to the cluster VIPs (or the standalone PSA device IP).
Profiler Configuration Migration
To export the Profiler configuration:
1.Select Maintenance > Import/Export > Import/Export Configuration > Profiler
2.Under Export, select the required option to export device data to backup file (CSV/binary) or profile modification to a backup file.
3.Click Export Data and save the file.
To import the IPS Profiler configurations:
1.Select Maintenance > Import/Export > Import/Export Configuration > Profiler.
2.Under Export, select the required option to import device data from backup file (CSV/binary) or profile modification from a backup file.
3.Click Browse, select the device data file and click Import Data.
Deprecated Features: ISA Gateway
To improve stability and overall security posture in new Ivanti Security Appliances, Ivanti has decided to deprecate old set of features. Deprecation list includes older versions of applications, authentication servers and few other features listed in the below table. This helps streamlining support to newer versions of applications for enhanced security and better performance.
Refer to Prerequisites for Migration and Supported Configuration Migration Path before starting the migration.
The configurations related to the unsupported features will be removed from the imported configuration as part of the migration. Policies referring to unsupported features will also be deleted after the migration.
For example, if a Host Checker policy is configured for statement of health check or Host Checker for Solaris, such rules present in those policies are removed and the policy will remain intact with other rules after the migration.
•Deprecated Features in Connect Secure
•Deprecated Features in Policy Secure
|
The following features are not supported in ISA Gateway: •Citrix web interface/JICA •Citrix StoreFront •Microsoft OWA 2000, 2003,2007 •IBM Lotus iNotes 5, 6, 6.5 •Sensors •Cloud App Visibility (CAV) •Telnet and SSH Resource profile •SDP •Connect Secure Wizards (User Access Policy) •Support for SRX Pulse client •Host checker (HC) for Solaris •HC - Custom Rule on Windows - Statement of Health •HC - Cache Cleaner •Pulse Collaboration •Pulse One Integration •Hob Java RDP •Unix file sharing •Basic HTML5 The deprecated features and the corresponding dependent configurations will be deleted post migration and the admin can view them under the event logs in the ISA Gateway. |
The following auth servers supported in PSA Gateway will be unsupported in ISA Gateway post migration: •SiteMinder •NIS •Anonymous •LDAP - Novell eDirectory •LDAP – iPlanet •MDM Server with type as PWS The migration fails if Legacy AD is configured on PSA Gateway, the configurations need to be moved to regular AD before migrating it to ISA Gateway. IMPORTANT: The realms/sign-in policies configured with these auth servers will not work on ISA Gateway.
|
Sample Screens of Connect Secure
|
Deprecated Features in Connect Secure |
PSA Gateway |
ISA Gateway |
|---|---|---|
|
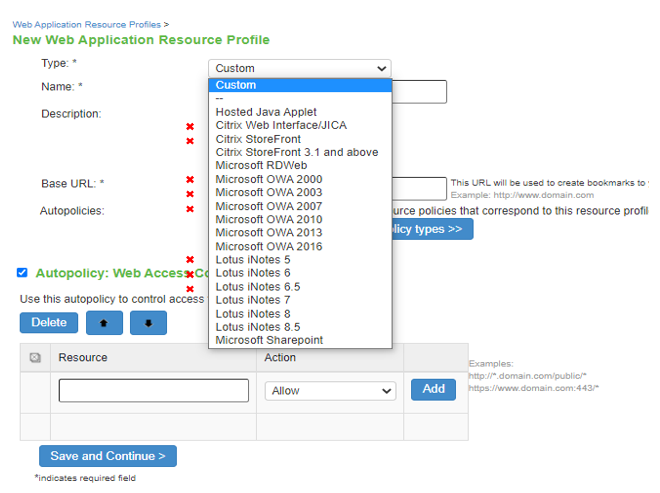
Web Profiles |
The screen shows the web application resource profiles on a PSA Gateway. The resource profiles marked with a red crossmark are deprecated on the ISA Gateway.
|
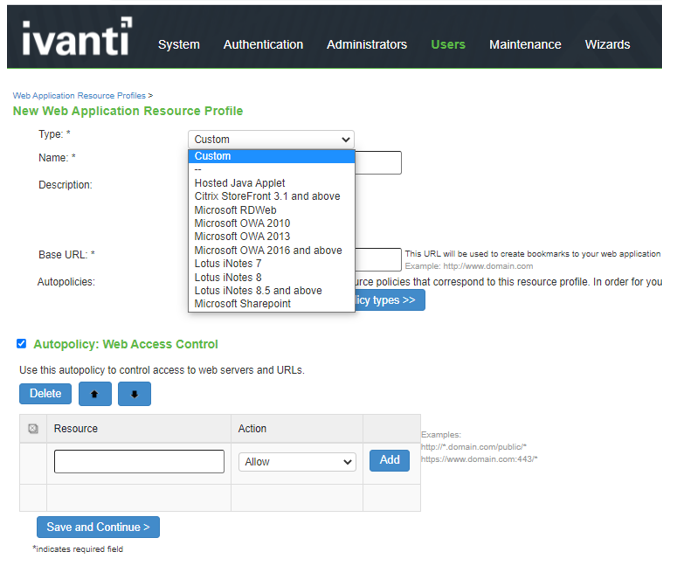
The screen shows the web application resource profiles on ISA Gateway.
|
|
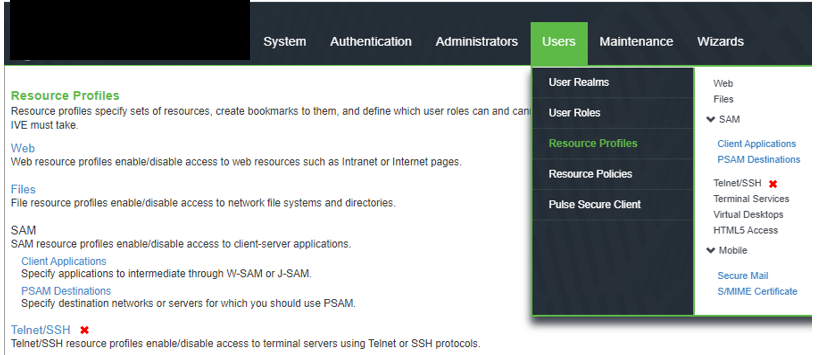
Resource Profiles |
The screen shows the resource profiles on PSA Gateway. The Telnet SSH resource profile marked in red is deprecated in ISA Gateway.
|
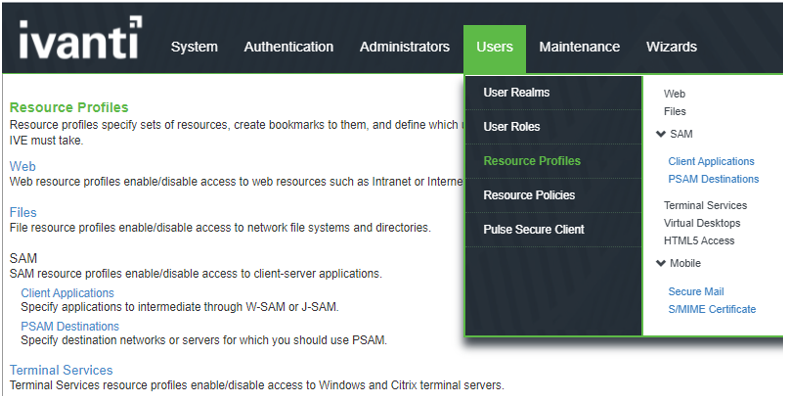
The screen shows the Resource profiles on ISA Gateway.
|
|
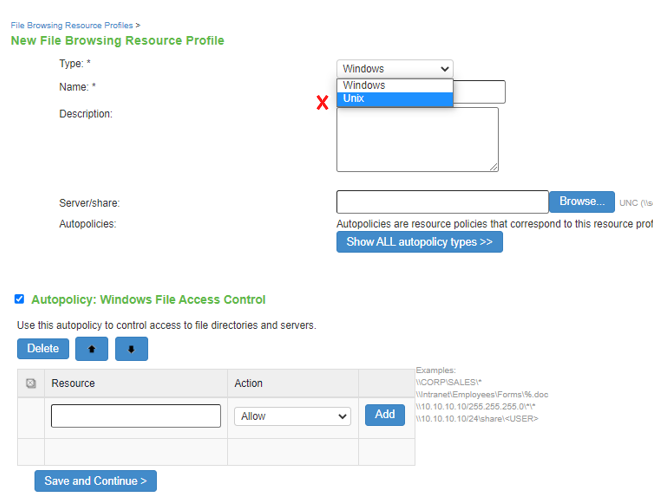
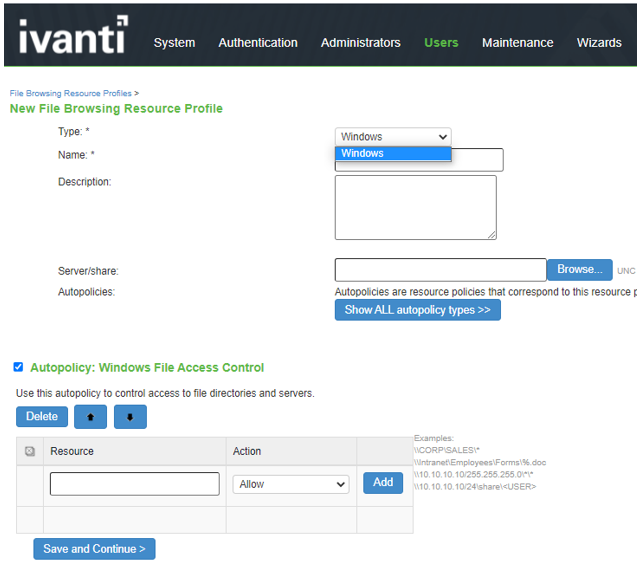
Resource Profiles- File Types |
The screen shows the resource profiles on PSA Gateway. The Unix Resource Profile -file type marked in red is deprecated in ISA Gateway . |
The screen shows the ResourceProfile - File type on ISA Gateway.
|
|
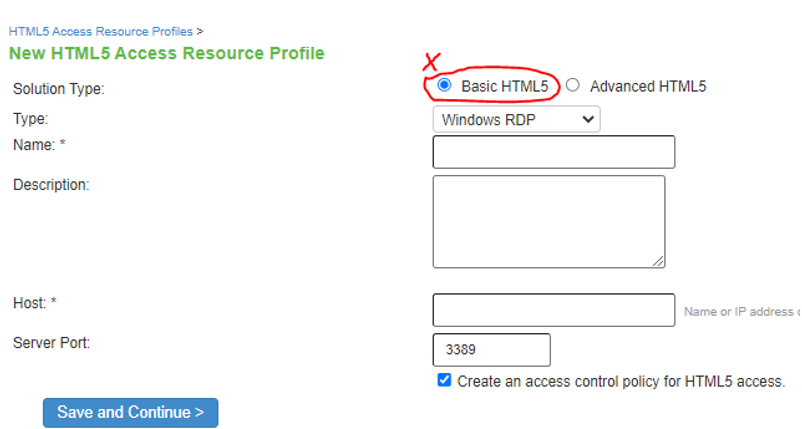
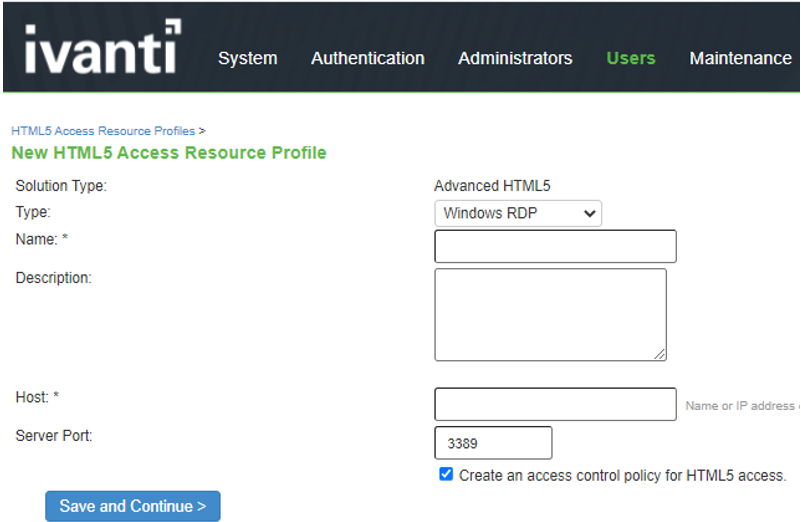
Resource Profiles- HTML 5 |
The screen shows the resource profiles on PSA Gateway. The Basic HTML5 Resource Profile marked in red is deprecated in ISA Gateway.
|
The screen shows the ResourceProfile - HTML5 on ISA Gateway.
|
|
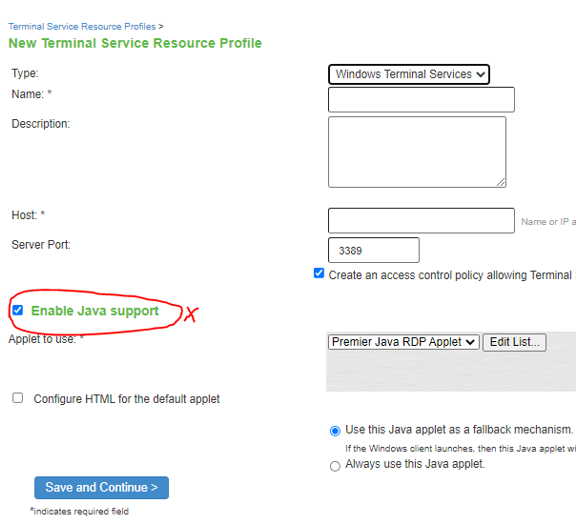
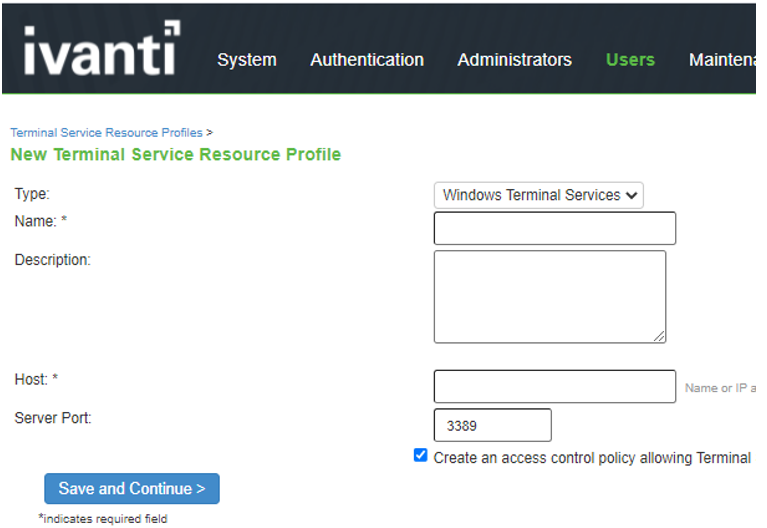
Resource Profile - Terminal Services |
The screen shows the resource profiles on PSA Gateway. The Java Support marked in red is deprecated in ISA Gateway.
|
The screen shows the ResourceProfile - Terminal Service on ISA Gateway.
|
|
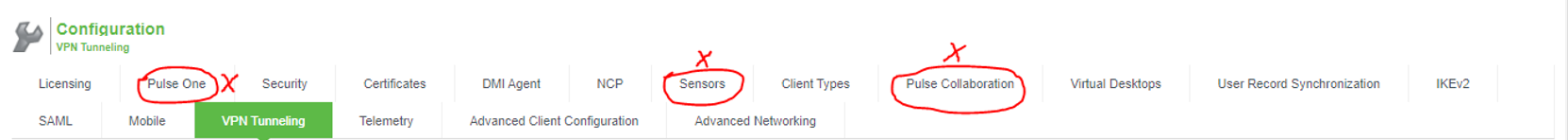
Config List |
The screen shows the VPN tunneling configuration options on PSA Gateway. The options highlighted in red are deprecated on ISA Gateway.
|
The screen shows the option newly added in the PSA Gateway.
|
|
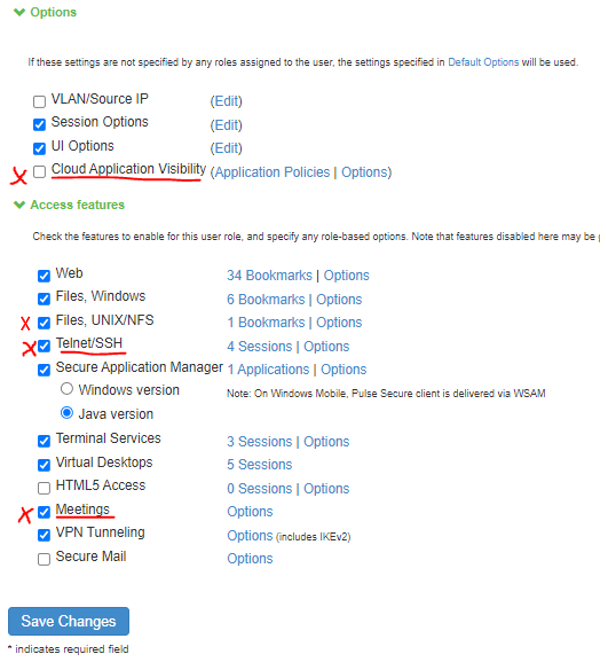
User Role Options |
The screen shows the settings on PSA Gateway. The options highlighted in red are deprecated on ISA Gateway.
|
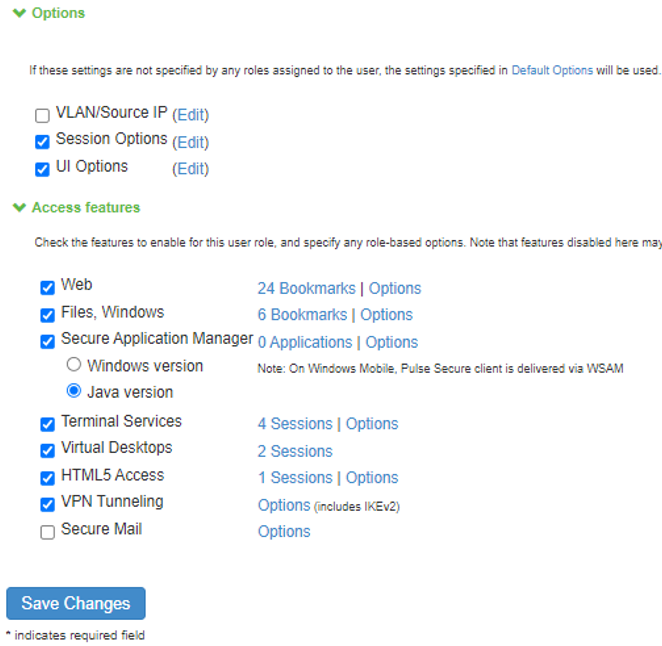
The screen shows the settings on the ISA Gateway.
|
|
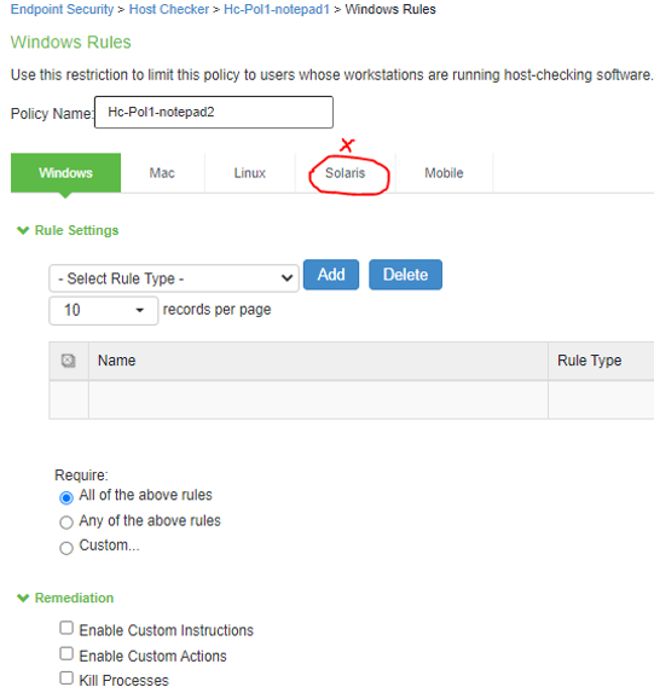
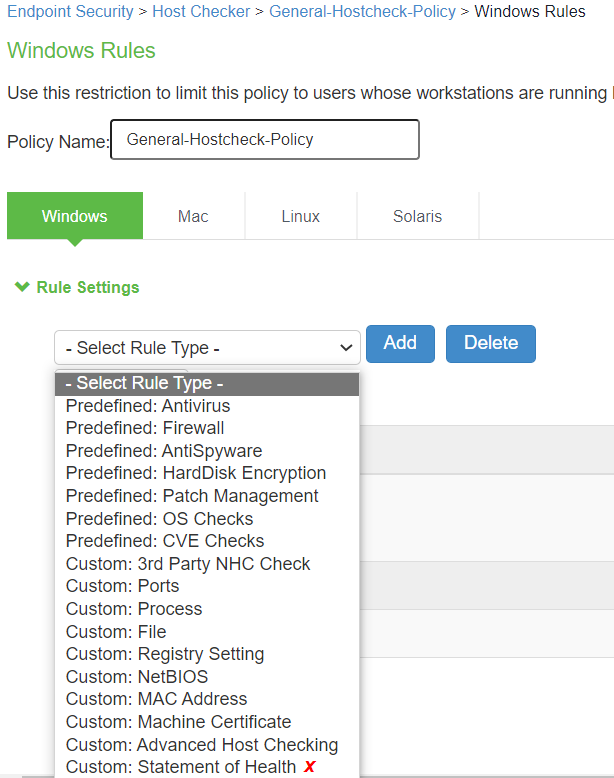
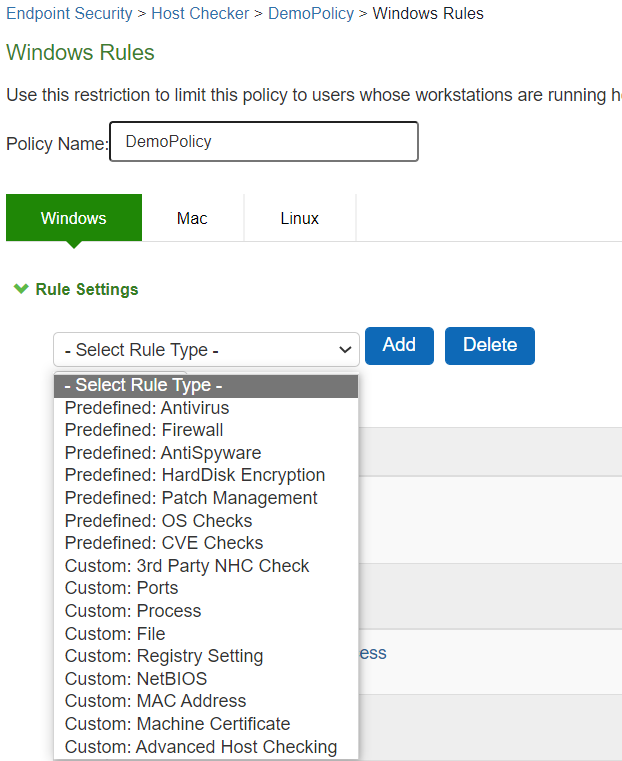
HC Policy OS |
The screen shows the Host Checker (HC) options on PSA Gateway. The Solaris option highlighted in red is deprecated in ISA Gateway.
|
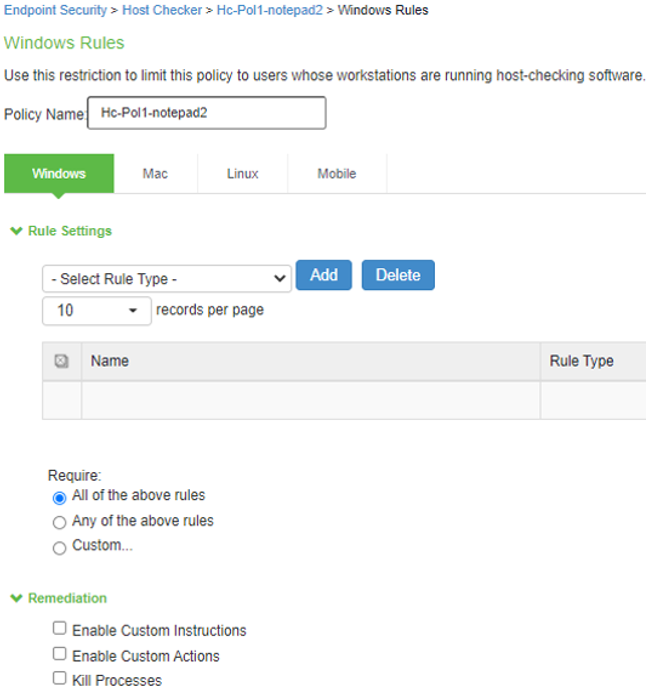
The screen shows the HC options on ISA Gateway.
|
|
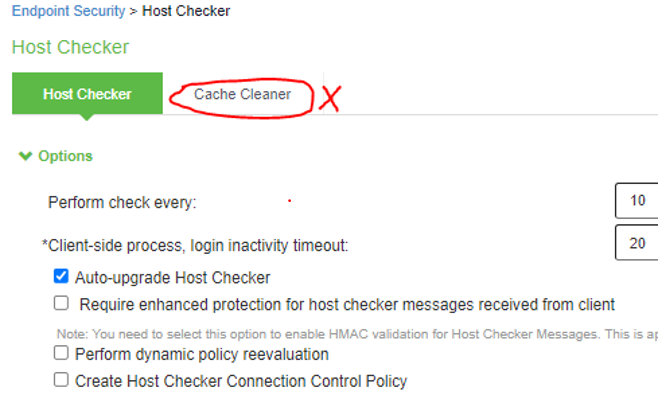
HC - Cache Cleaner |
The screen shows the Host Checker on PSA Gateway. The Cache Cleaner marked in red is deprecated in ISA Gateway.
|
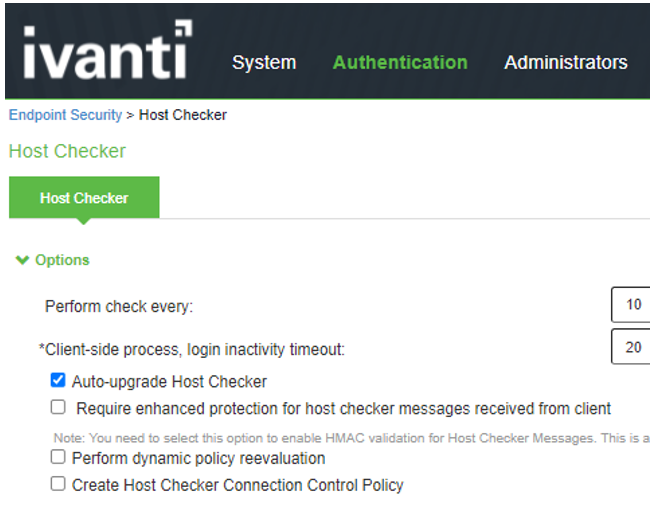
The screen shows the HC options on ISA Gateway.
|
|
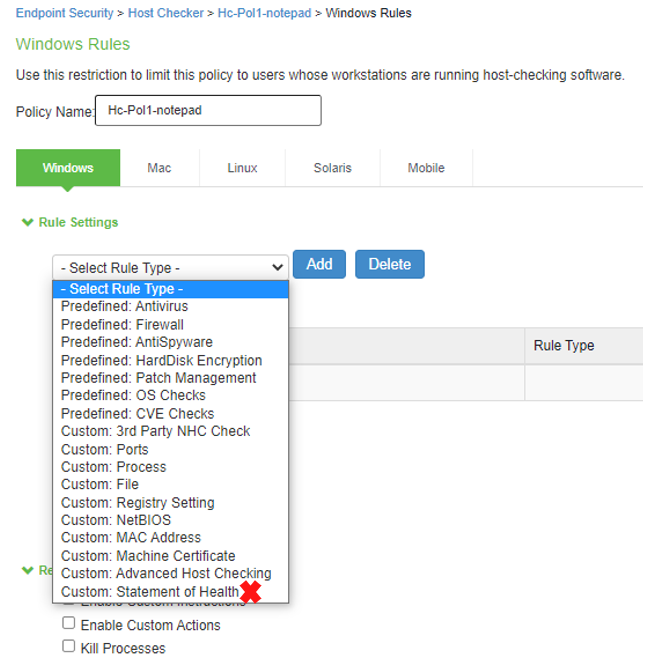
HC - Statement of Health |
The screen shows the Host Checker on PSA Gateway. The Statement of health marked in red is deprecated in ISA Gateway.
|
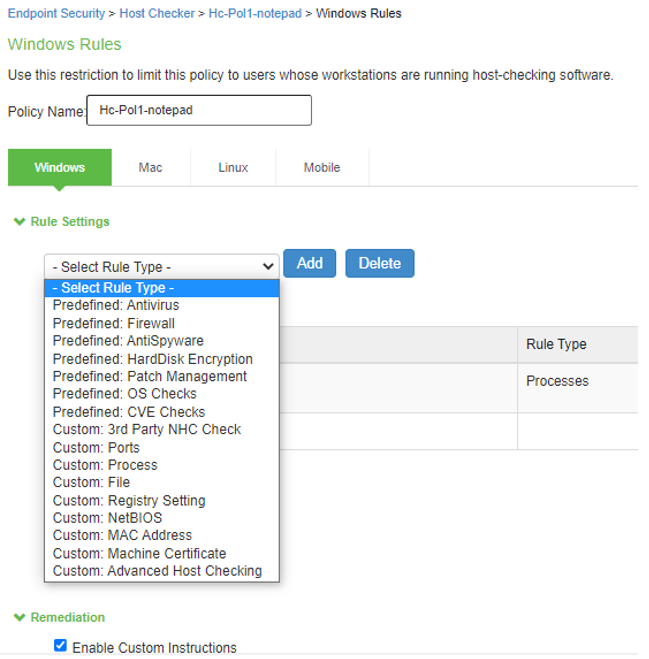
The screen shows the HC options on ISA Gateway. |
|
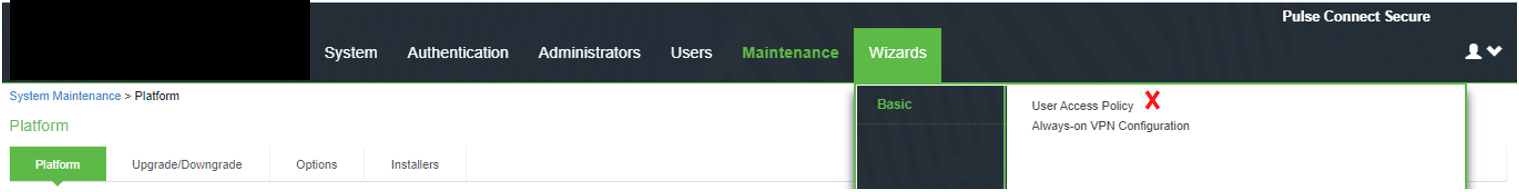
Wizard |
The screen shows the Host Checker on PSA Gateway. The User Access Policy marked in red is deprecated in ISA Gateway.
|
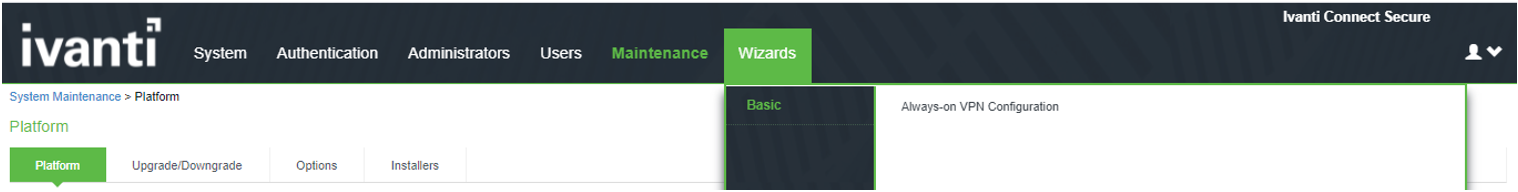
The screen shows the wizard on ISA Gateway.
|
|
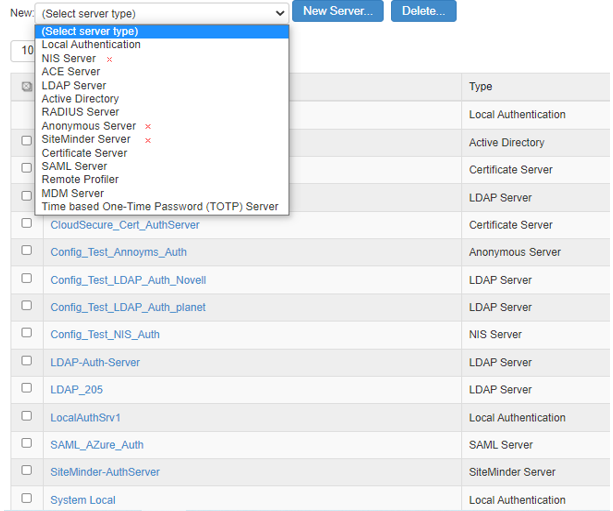
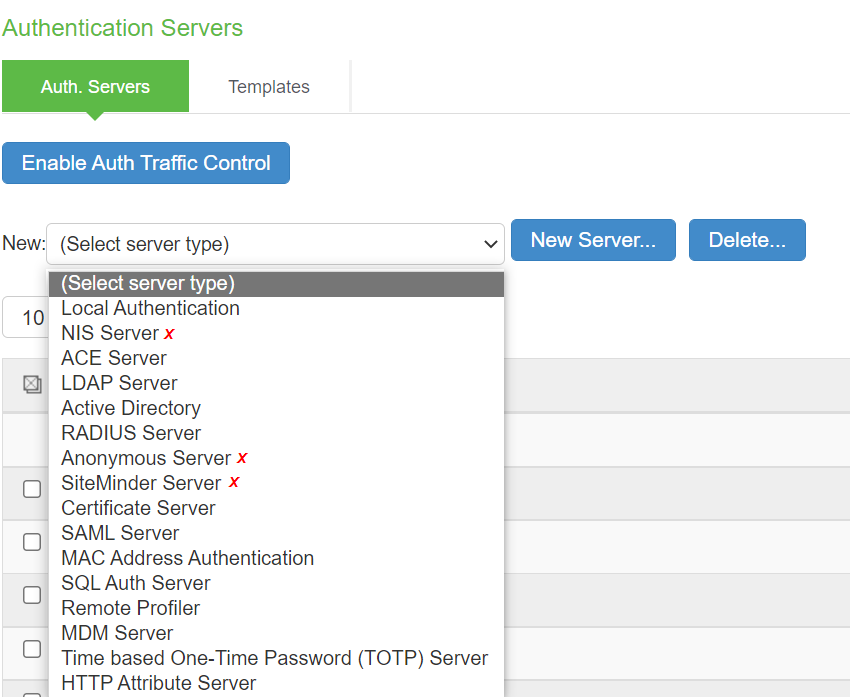
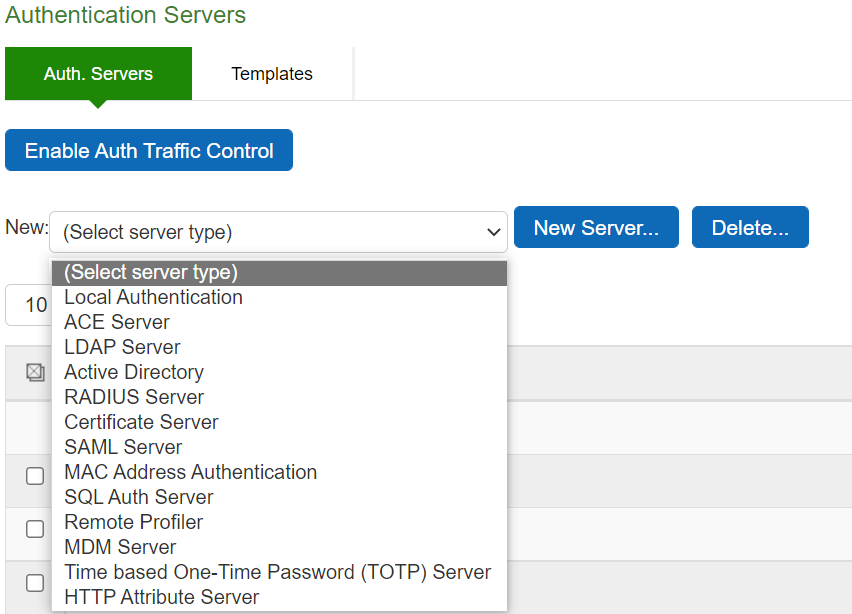
Auth Servers |
The screen shows the auth servers on a PSA Gateway. The auth servers marked with red crossmark are deprecated on ISA Gateway.
|
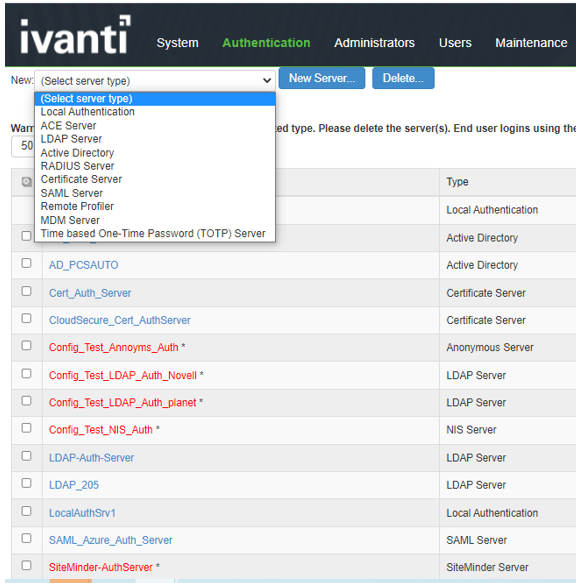
The screen shows the auth servers on ISA Gateway. The deprecated auth servers, which are migrated from PSA Gateway are shown in red with an asterrick. These servers have to be deleted manually as the enduser logins to these servers will be disabled.
|
|
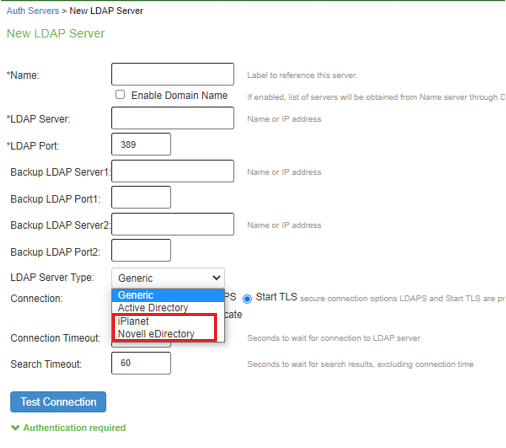
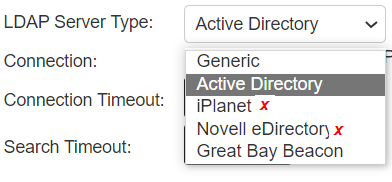
LDAP Auth Server Type |
The screen shows the LDAP auth server with different connection types on PSA Gateway. The connection type highlighted in Red are deprecated in ISA Gateway.
|
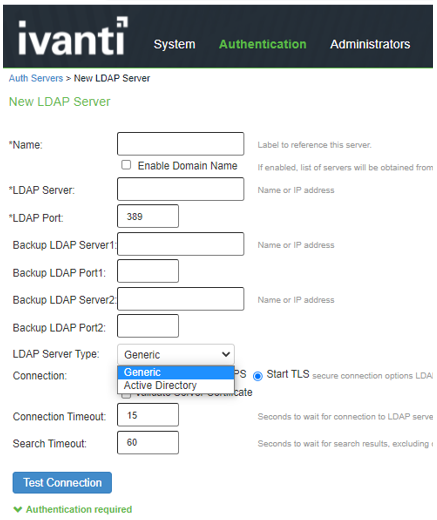
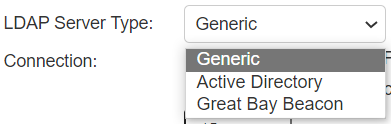
The screen shows the LDAP auth server on ISA Gateway.
|
|
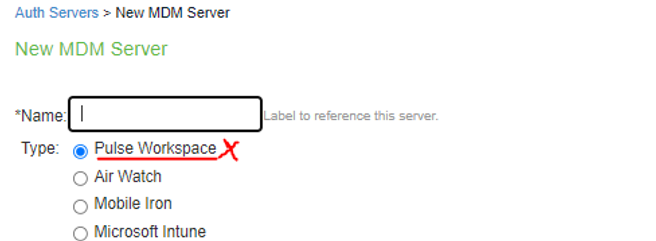
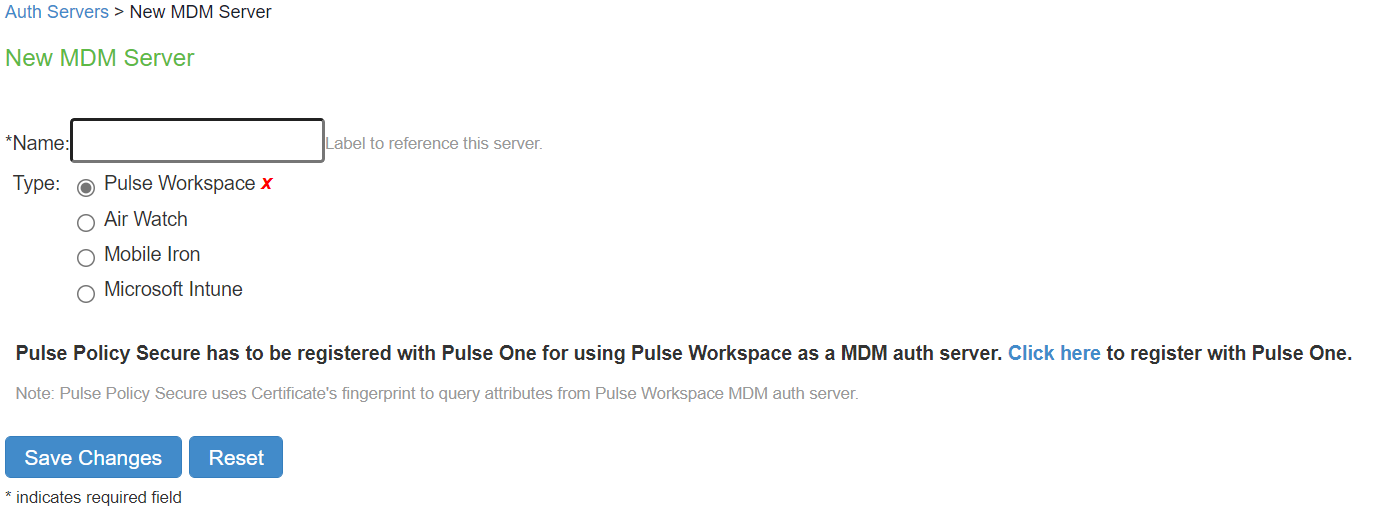
MDM Server |
The screen shows the MDM server with different connection types on PSA Gateway. The connection type highlighted in Red are deprecated in ISA Gateway
|
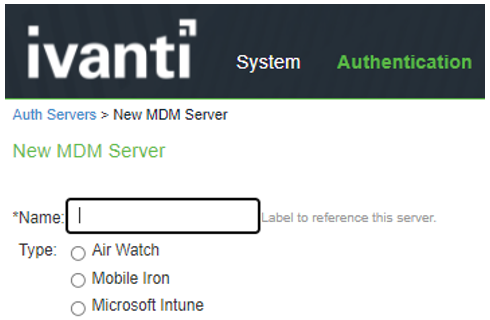
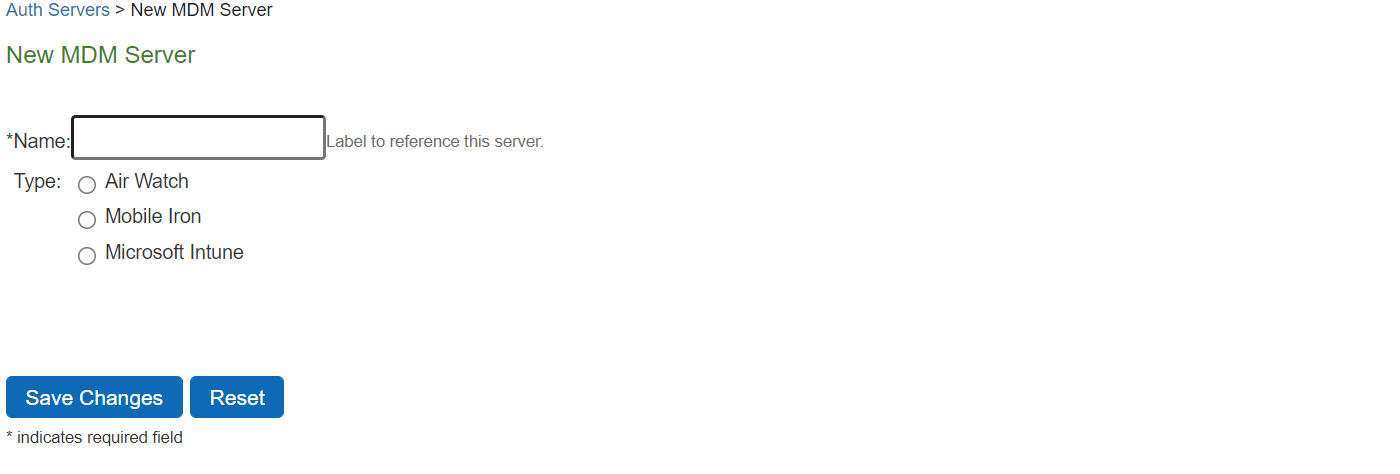
The screen shows the MDM server on ISA Gateway.
|
|
Hostcheck PASS messages |
Info AUT31504 2021-10-17 21:21:17 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[Files Role, HTML5 Role, STA Role, Terminal Services Role, VDI Role, Web Role, WSAM Role, All Core Features Role] - Login succeeded for username/All Core Features Realm (session:sid27ff58ec684a85a48b43280bad41f5200490e365dedf089c) from x.x.x.x . Info AUT22923 2021-10-17 21:21:13 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Host Checker policy 'Pulse Secure Endpoint Compliance' passed on host x.x.x.x for user 'username'. Info AUT24326 2021-10-17 21:20:23 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Secondary authentication successful for username/Google TOTP Auth Server from x.x.x.x Info AUT31666 2021-10-17 21:19:11 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Anomaly (new_location) found for username. Prompting for secondary authentication Info AUT24326 2021-10-17 21:19:11 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Primary authentication successful for username/PSBNG-LDAP from x.x.x.x |
Info AUT30544 2021-10-17 21:47:36 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - User chose to proceed on the sign-in notification page "Post-sign-In Notification" Info AUT31984 2021-10-17 21:47:24 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Host Checker Compliance Result - ['Fully Compliant'] on host ['x.x.x.x'] from address [''] for user ['username'], passed_hc_policies:['Pulse Secure Endpoint Compliance'], failed_hc_policies:[''], failed_reasons: ['']. Info AUT22923 2021-10-17 21:47:24 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Host Checker policy 'Pulse Secure Endpoint Compliance' passed on host x.x.x.x for user 'username'. Info AUT24326 2021-10-17 21:46:47 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Secondary authentication successful for username/Google TOTP Auth Server from x.x.x.x Info AUT31666 2021-10-17 21:46:40 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Anomaly (new_location) found for username. Prompting for secondary authentication Info AUT24326 2021-10-17 21:46:40 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Primary authentication successful for username/PSBNG-LDAP from x.x.x.x |
|
HostCheck FAIL messages |
Info AUT22925 2021-10-17 21:33:00 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Host Checker policy 'Pulse Secure Endpoint Compliance' failed on host x.x.x.x . Reason: 'Rule-Compliance-WIN-AS:Windows Defender 6.1.7600.16385 does not comply with policy. Compliance requires real time protection enabled.; Rule-Compliance-WIN-FW:Windows Firewall 6.1.7600.16385 does not comply with policy. Compliance requires firewall to be turned on.; Rule-Compliance-WIN-AV:Windows Defender 6.1.7600.16385 does not comply with policy. Compliance requires real time protection enabled and latest virus definitions and successful complete system scan.'. Info AUT24326 2021-10-17 21:32:23 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Secondary authentication successful for username/Google TOTP Auth Server from x.x.x.x Info AUT31760 2021-10-17 21:32:10 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Detected first time login for user 'username'. Prompting for secondary authentication. Info AUT24326 2021-10-17 21:32:10 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Primary authentication successful for username/PSBNG-LDAP from x.x.x.x |
Info AUT31984 2021-10-17 22:46:03 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Host Checker Compliance Result - ['Fully Non Compliant'] on host ['x.x.x.x'] from address [''] for user ['username'], passed_hc_policies:[''], failed_hc_policies:['Pulse Secure Endpoint Compliance'], failed_reasons: ['Rule-Compliance-WIN-AS:Anti-Spyware software listed in security requirements is not installed.; Rule-Compliance-WIN-AV:Anti-Virus software listed in security requirements is not installed.']. Info AUT22925 2021-10-17 22:46:03 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Host Checker policy 'Pulse Secure Endpoint Compliance' failed on host x.x.x.x . Reason: 'Rule-Compliance-WIN-AS:Anti-Spyware software listed in security requirements is not installed.; Rule-Compliance-WIN-AV:Anti-Virus software listed in security requirements is not installed.'. Info AUT24326 2021-10-17 22:45:21 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Secondary authentication successful for username/Google TOTP Auth Server from x.x.x.x Info AUT31666 2021-10-17 22:45:02 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Anomaly (new_location) found for username. Prompting for secondary authentication Info AUT24326 2021-10-17 22:45:02 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Primary authentication successful for username/PSBNG-LDAP from x.x.x.x |
|
The following features are not supported in ISA Gateway: 1.Sensors feature in IPS 2.Cache Cleaner 3.Basic authentication Policy Wizard. 4.Host checker (HC) for Solaris. 5.HC - Custom Rule on Windows - Statement of Health
The deprecated features and the corresponding dependent configurations will be deleted post migration and the admin can view them under the event logs in the ISA Gateway. |
The following auth servers supported in PSA Gateway will be unsupported in ISA Gateway post migration:
•SiteMinder •NIS •Anonymous •LDAP - Novell eDirectory •LDAP – iPlanet •MDM Server with type as PWS IMPORTANT: The realms/sign-in policies configured with these auth servers will not work on ISA Gateway.
|
Sample Screens of Policy Secure
|
Deprecated Features in Policy Secure |
PSA Gateway |
ISA Gateway |
|---|---|---|
|
HC Policy OS |
The screen shows the Host Checker (HC) options on PSA Gateway. The Solaris option highlighted in red is deprecated in ISA Gateway.
|
The screen shows the HC options on ISA Gateway.
|
|
HC - Cache Cleaner |
The screen shows the Host Checker on PSA Gateway. The Cache Cleaner marked in red is deprecated in ISA Gateway.
|
The screen shows the HC options on ISA Gateway.
|
|
HC - Statement of Health |
The screen shows the Host Checker on PSA Gateway. The Statement of health marked in red is deprecated in ISA Gateway.
|
The screen shows the HC options on ISA Gateway. |
|
Wizard |
The screen shows the Host Checker on PSA Gateway. The User Access Policy marked in red is deprecated in ISA Gateway.
|
The screen shows the wizard on ISA Gateway.
|
|
Auth Servers |
The screen shows the auth servers on a PSA Gateway. The auth servers marked with red crossmark are deprecated on ISA Gateway.
|
The screen shows the auth servers on ISA Gateway. The deprecated auth servers, which are migrated from PSA Gateway are shown in red with an asterrick. These servers have to be deleted manually as the enduser logins to these servers will be disabled.
|
|
LDAP Auth Server Type |
The screen shows the LDAP auth server with different connection types on PSA Gateway. The connection type highlighted in Red are deprecated in ISA Gateway.
|
The screen shows the LDAP auth server on ISA Gateway.
|
|
MDM Server |
The screen shows the MDM server with different connection types on PSA Gateway. The connection type highlighted in Red are deprecated in ISA Gateway
|
The screen shows the MDM server on ISA Gateway.
|
|
Hostcheck PASS messages |
Info AUT31504 2021-10-17 21:21:17 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[Files Role, HTML5 Role, STA Role, Terminal Services Role, VDI Role, Web Role, WSAM Role, All Core Features Role] - Login succeeded for username/All Core Features Realm (session:sid27ff58ec684a85a48b43280bad41f5200490e365dedf089c) from x.x.x.x . Info AUT22923 2021-10-17 21:21:13 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Host Checker policy 'Pulse Secure Endpoint Compliance' passed on host x.x.x.x for user 'username'. Info AUT24326 2021-10-17 21:20:23 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Secondary authentication successful for username/Google TOTP Auth Server from x.x.x.x Info AUT31666 2021-10-17 21:19:11 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Anomaly (new_location) found for username. Prompting for secondary authentication Info AUT24326 2021-10-17 21:19:11 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Primary authentication successful for username/PSBNG-LDAP from x.x.x.x |
Info AUT30544 2021-10-17 21:47:36 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - User chose to proceed on the sign-in notification page "Post-sign-In Notification" Info AUT31984 2021-10-17 21:47:24 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Host Checker Compliance Result - ['Fully Compliant'] on host ['x.x.x.x'] from address [''] for user ['username'], passed_hc_policies:['Pulse Secure Endpoint Compliance'], failed_hc_policies:[''], failed_reasons: ['']. Info AUT22923 2021-10-17 21:47:24 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Host Checker policy 'Pulse Secure Endpoint Compliance' passed on host x.x.x.x for user 'username'. Info AUT24326 2021-10-17 21:46:47 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Secondary authentication successful for username/Google TOTP Auth Server from x.x.x.x Info AUT31666 2021-10-17 21:46:40 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Anomaly (new_location) found for username. Prompting for secondary authentication Info AUT24326 2021-10-17 21:46:40 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Primary authentication successful for username/PSBNG-LDAP from x.x.x.x |
|
HostCheck FAIL messages |
Info AUT22925 2021-10-17 21:33:00 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Host Checker policy 'Pulse Secure Endpoint Compliance' failed on host x.x.x.x . Reason: 'Rule-Compliance-WIN-AS:Windows Defender 6.1.7600.16385 does not comply with policy. Compliance requires real time protection enabled.; Rule-Compliance-WIN-FW:Windows Firewall 6.1.7600.16385 does not comply with policy. Compliance requires firewall to be turned on.; Rule-Compliance-WIN-AV:Windows Defender 6.1.7600.16385 does not comply with policy. Compliance requires real time protection enabled and latest virus definitions and successful complete system scan.'. Info AUT24326 2021-10-17 21:32:23 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Secondary authentication successful for username/Google TOTP Auth Server from x.x.x.x Info AUT31760 2021-10-17 21:32:10 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Detected first time login for user 'username'. Prompting for secondary authentication. Info AUT24326 2021-10-17 21:32:10 - NODE_3_3 - [x.x.x.x] username(All Core Features Realm)[] - Primary authentication successful for username/PSBNG-LDAP from x.x.x.x |
Info AUT31984 2021-10-17 22:46:03 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Host Checker Compliance Result - ['Fully Non Compliant'] on host ['x.x.x.x'] from address [''] for user ['username'], passed_hc_policies:[''], failed_hc_policies:['Pulse Secure Endpoint Compliance'], failed_reasons: ['Rule-Compliance-WIN-AS:Anti-Spyware software listed in security requirements is not installed.; Rule-Compliance-WIN-AV:Anti-Virus software listed in security requirements is not installed.']. Info AUT22925 2021-10-17 22:46:03 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Host Checker policy 'Pulse Secure Endpoint Compliance' failed on host x.x.x.x . Reason: 'Rule-Compliance-WIN-AS:Anti-Spyware software listed in security requirements is not installed.; Rule-Compliance-WIN-AV:Anti-Virus software listed in security requirements is not installed.'. Info AUT24326 2021-10-17 22:45:21 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Secondary authentication successful for username/Google TOTP Auth Server from x.x.x.x Info AUT31666 2021-10-17 22:45:02 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Anomaly (new_location) found for username. Prompting for secondary authentication Info AUT24326 2021-10-17 22:45:02 - DFS_NODE_3_92 - [x.x.x.x] Default Network::username(All Core Features Realm)[][] - Primary authentication successful for username/PSBNG-LDAP from x.x.x.x |