Introduction
Scope
The Ivanti Connect Secure Administrator Guide provides detailed information on configuring, authenticating, securing, managing, and troubleshooting Ivanti Connect Secure and Ivanti Secure Access Client in your environment. Before you configure your environment, it is mandatory to walk through the Supported Platforms Guide and the License Management Guide.
Ivanti Connect Secure Documentation and Resources
The Ivanti Connect Secure documentation set includes multiple separate deliverables in the web HTML format. The publications are available at https://www.ivanti.com/support/product-documentation.
Key Terms and Concepts
|
Glossary Acronyms |
Description |
|
AAA Server |
AAA is expanded as Authentication, Authorization, and Accounting. AAA Server is a server program which provides any of the AAA services, viz, Authentication, Authorization or Accounting. |
|
Access |
Refers to the level and the extent of a service's functionality or data that a user is entitled to use. |
|
CIE |
Content Intermediation Engine. An advanced parser and rewriter that retrieves Web-based content from internal Web servers and changes URL references and Java socket calls. |
|
Cipher |
Cipher is an algorithm for performing encryption or decryption. It is a series of well-defined steps that can be followed as a procedure. |
|
Compression |
A method that is followed by the ICS to improve the performance by compressing common types of Web and file data such as HTML files, Word documents, and images |
|
Digital Certificates |
Digital Certificates are issued by Certificate Authority (CA). A digital certificate validates the ownership of a public key with subject name in the certificate. |
|
DMI |
Device Management Interface is an XML-RPC based protocol that is used to manage Ivanti Connect Secure devices. |
|
HMAC Key |
Hash Message Authentication Code is a specific type of message authentication code (MAC) hashed to identify individual devices to the application. |
|
Host Checker |
Host Checker is an endpoint security-based feature, which performs security and system integrity checks that pre-qualify endpoints before allowing access to the network's resources. |
|
IDPS |
Intrusion detection and prevention sensor monitors networks to detect suspicious and anomalous network traffic based on specific rules defined in IDP rule bases. |
|
IF-MAP |
Interface for Metadata Access Point is a protocol defined by the Trusted Network Connect Working Group (TNC-WG) as a standard interface between different network elements and devices. |
|
Localization |
The multi-language support provided by the ICS for file encoding, end-user interface display, and customized sign-in and system pages |
|
Non-broadcast SSID |
Non-broadcast Service Set Identifier prevents unauthorized users from being able to detect the wireless network from their wireless clients. |
|
Realm |
Specifies the authentication and authorization mechanisms (including Host Checker policies) associated with a given sign-in URL. |
|
Roles |
Specifies the user privileges and access mechanism based on the information returned by the realm's directory or the user's name. |
|
Sign-In Policy |
Sign-in policies define the URLs that users and administrators use to access the device and the sign-in pages. |
|
SMS |
System Management Server provides automatic updates to non-compliant software. |
Ivanti Connect Secure Overview
Ivanti Connect Secure gives employees, partners and customers secure and controlled access to corporate data and applications. The applications include file servers, web servers, native messaging, and hosted servers outside your trusted network.
The organization home page can be accessed by employees, partners and customers through a web browser with SSL support and an Internet connection. The page allows the users to:
•Securely browse web or file servers
•Use HTML-enabled enterprise applications
•Start the client/server application proxy
•Begin a Windows, Citrix, or Telnet/SSH terminal session
•Access corporate e-mail servers
•Start a secured Layer 3 tunnel
•Schedule or attend a secure Online meeting
How Ivanti Connect Secure Works
Ivanti Connect Secure authorizes the resources that are accessed by users through an extranet session hosted by the appliance. Ivanti Connect Secure intermediates the data that flows between external users and the company's internal resources to provide robust security. The following diagram is an example of Ivanti Connect Secure within a LAN environment.
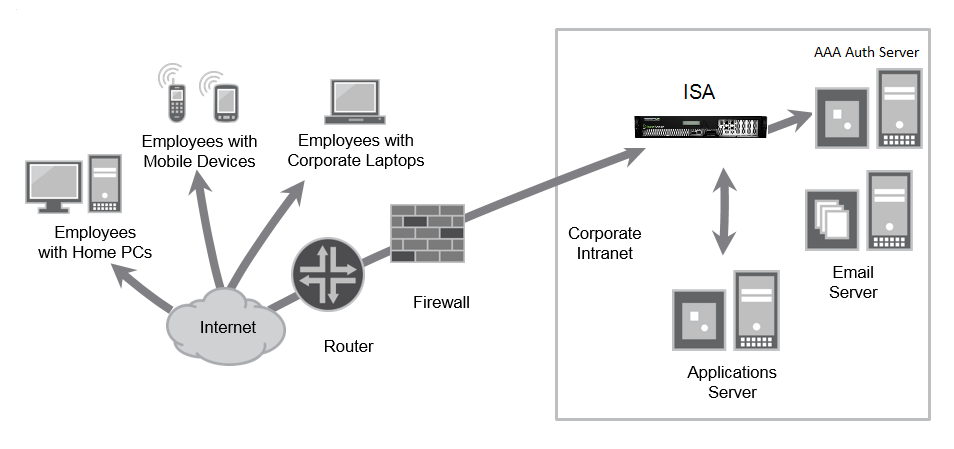
During the process of intermediation, the ICS receives secure requests from the external, authenticated users and makes the request to the internal resources on behalf of the users. By intermediating, the need to deploy extranet toolkits in traditional demilitarized zones (DMZ) or provision a remote access VPN for employees is eliminated.
Ivanti Connect Secure Benefits
Ivanti Connect Secure offers high standard configurable solutions. Ivanti Connect Secure:
•Intermediates access to multiple types of applications and resources. These include web-based enterprise applications, Java applications, file shares, terminal hosts, and other client/server applications such as Microsoft Outlook, Lotus Notes, the Citrix XenApp and Smart Phones. Additionally, administrators can provision an access method that allows full Layer 3 connectivity, which provides the same level of access that a user would get if they were on the corporate LAN.
•Fine tunes the user access to the appliance, resource types, or individual resources based on factors such as group membership, source IP address, certificate attributes, and endpoint security status. For example, you can use the dual-factor authentication and client-side digital certificates to authenticate users and use LDAP group membership to authorize users to access individual applications.
•Assesses the security status of your users' computers by checking for endpoint defense tools such as current antivirus software, firewalls, and security patches. You can then allow or deny users access to the appliance, resource types, or individual resources based on the computer's security status.
•Acts as a secure application Layer gateway intermediating all requests between the public Internet and internal corporate resources. All requests that enter the ICS are encrypted by the end user's browser using SSL/TLS. Because the ICS provides a robust security layer between the public Internet and internal resources, administrators do not need to constantly manage security policies and patch security vulnerabilities for numerous different applications and web servers deployed in the public-facing DMZ.
Using Ivanti Connect Secure for Securing Traffic
Ivanti Connect Secure provides secure access to different types of applications, servers and other resources through its remote access mechanism. Simply select both the resources you want to secure and the appropriate access mechanism.
As an example, if you want secure access to Microsoft Outlook, you can use the Secure Application Manager (SAM). The Secure Application Manager intermediates traffic to the client/server applications including Microsoft Outlook, Lotus Notes, and Citrix. Otherwise, if you want to secure access to your company Intranet websites, you can use the web rewriting feature. This feature uses the ICS's Content Intermediation Engine to intermediate traffic to web-based applications and web pages.
Intermediating Traffic Types
The remote access mechanism is integrated with the ICS to intermediate the following types of traffic, the application and the resources that it handles.
•Web applications and web pages: Use the web rewriting feature to intermediate web page type of content. The web rewriting feature includes templates that enables you to easily configure access to applications such as Citrix, OWA, Lotus iNotes, and SharePoint. In addition, you can use the web rewriting custom configuration option to intermediate traffic from a wide variety of additional web-based applications, web pages, and custom-built web applications.
•Web applications using Java applets: Use the hosted Java applets feature to intermediate this type of content. This feature enables the user to host Java applets and the HTML pages that they reference directly on Ivanti Connect Secure rather than maintaining a separate Java server.
•File servers and directories using file traffic: Uses the file rewriting feature to intermediate and dynamically "webify" access to file shares. The file rewriting feature enables you to secure traffic to a variety of Windows servers, directories, and file shares.
•Client/server applications: Use the Secure Application Manager (SAM) feature to intermediate this type of content. SAM comes in two varieties (PSAM and JSAM). The PSAM and JSAM features include templates that enable you to easily configure access to applications such as Lotus Notes, Microsoft Outlook, NetBIOS file browsing, and Citrix. In addition, you can use the PSAM and JSAM custom configuration options to intermediate traffic from a wide variety of additional client/server applications and destination networks.
•Windows Terminal Servers and Citrix server terminal emulation sessions: Use the Terminal Services feature to intermediate this type of content. This feature enables you to easily configure access to Windows Terminal Servers, Citrix XenApp and StoreFront servers. You can also use this feature to deliver the terminal services clients directly from the ICS, eliminating the need to use another web server to host the clients.
•All network traffic: Use the VPN Tunneling feature to create a secure, Layer 3 tunnel over the SSL connection, allowing access to any type of application available on the corporate network. This feature easily connects remote users into your network by tunneling network traffic over port 443, enabling the users with complete access to all network resources without configuring access to individual servers, applications, and resources. Layer 3 VPN tunnels can be initiated using the integrated Network Connect client and the Ivanti Secure Access Client.
Authenticating Users with Existing Servers
You can easily configure Ivanti Connect Secure to use your company's existing servers to authenticate your end users. Users need not create a new username and password to access the device.
The ICS supports integration with LDAP, RADIUS, Windows NT Domain, Active Directory, SAML, and RSA ACE/Servers.
Alternatively, if you do not want to use one of these standard servers, you can store usernames and credentials directly on the ICS and use it as an authentication server. In addition, you can choose to authenticate users based on attributes contained in authentication assertions generated by SAML authorities or client-side certificates.
Also, if you do not want your users to sign into the device, you can use the anonymous authentication server, which allows users to access the device without providing a username or password.
Ivanti Secure Access Client supports only one case of dual-factor authentication, in which the client certificate is the primary, while the local authorization is the secondary.
Using Client-side Authorization to Control Access
In addition to using authentication servers to control access to Ivanti Connect Secure, you can control access to the ICS and the resources it intermediates using a variety of additional client-side checks. Ivanti Connect Secure enables you to create a multi-layered approach to protect itself and your resources by doing the following:
1.As a first step, perform pre-authentication checks that control user access to the ICS's sign-in page. For example, you might configure the ICS to check whether or not the user's computer is running a particular version of Norton Antivirus. In the event it is not running, you can determine that the user's computer is unsecure and disable access to the ICS's sign-in page until the user has updated the computer's antivirus software.
2.After the user has successfully accessed the ICS's sign-in page, realm-level checks are performed to determine whether the ICS's end-user home page is accessed. The most common realm-level check is performed by an authentication server. The server determines whether the user enters a valid username and password. You can perform other types of realm-level checks such as checking if the user's IP address is in your network or that the user is using the web browser type that you have specified.
3.If the user does not get through the realm-level checks that are specified, the user is not allowed to sign in, or a “stripped down” version of the home page is displayed. Generally, this stripped-down version contains significantly less functionality than what is available to your standard users because the user has not passed all the authentication criteria. The ICS provides extremely flexible policy definitions, enabling you to dynamically alter end-user resource access based on corporate security policies.
4.After the ICS successfully assigns a user to a realm, the appliance maps the user to a role based on your selection criteria. A role specifies which access mechanisms a selected group of users can access. It also controls session and UI options for that group of users. You can use a wide variety of criteria to map users to roles. For example, you can map users to different roles based on endpoint security checks or attributes obtained from an LDAP server or client-side certificate.
5.In most cases, a user's role assignments control which individual resources the user can access. For example, you might configure access to your company's Intranet page using a web resource profile and then specify that all members of the Employees role can access that resource.
6.However, you can choose to further fine tune access to individual resources. For example, you may enable members having the Employees role to access your company's Intranet (as described earlier), also add a resource policy detailed rule that requires users to meet additional criteria to access the resource. An additional example would be, you may require users to be members of the employees' role and to sign into the device during business hours to access your company Intranet.
Integration between Ivanti Connect Secure and the Resources It Intermediates
In a typical configuration, you can add bookmarks directly to the ICSs end-user home page. The bookmarks that you add are links to the resources that you configure the ICS to intermediate. Adding these bookmarks enables the users to sign into the Ivanti Connect Secure and find a consolidated list of resources available for them. Within this typical configuration, you can streamline the integration between the ICS and the intermediated resources by enabling single sign-on (SSO).
SSO is a process that allows pre-authenticated users to access other applications or resources that are protected by another access management system without having to re-enter their credentials. During system configuration, you can enable SSO by specifying user credentials that you want the ICS to pass to the intermediated resources. Alternatively, if you do not want to centralize user resources on the ICS's end-user home page, you can create links to the intermediated resources from another web page.
To cite an example, you can configure bookmarks on Ivanti Connect Secure, and then add links to those bookmarks from your company's Intranet. Your users can then sign into your company's Intranet and click the links there to access the intermediated resources without going through the ICS's home page. As with standard Ivanti Connect Secure bookmarks, you can enable SSO for these external links.
Using Host Checker to Protect from Threats
The Host Checker feature in Ivanti Connect Secure protects the ICS against viruses, attacks, and other security concerns. Host Checker performs security checks on the clients that connect to the device.
Host Checker can:
•Verify if the end-user system contains up-to-date antivirus software, firewalls, critical software hotfixes, and other applications that protect your users' computers.
•Enable or deny users' access to the ICS's sign-in pages, realms, roles, and resources based on the results that Host Checker returns. Alternatively, you can display the recovery instructions to users, so they can bring their computers into compliance.
•Secure your network from hostile outside intrusion by integrating your device with a Juniper Networks Intrusion Detection and Prevention (IDP) sensor. You can use IDP devices to detect and block most network worms based on software vulnerabilities, non-file-based Trojan horses, the effects of Spyware, Adware, and Key Loggers, many types of malware, and zero-day attacks with anomaly detection.
Providing Redundancy in the Ivanti Connect Secure Environment
The Clustering feature in Ivanti Connect Secure ensures redundancy in your environment. With this feature you can:
•Deploy two or more appliances as a cluster, ensuring no user downtime in the rare event of failure and stateful peering that synchronizes user settings, ICS settings, and user session data.
•Support active/passive or active/active configurations across a LAN.
•In Active/Passive mode, one device actively serves user requests while the other device runs passively in the background to synchronize state data. If the active device goes offline, the passive device automatically starts servicing user requests.
•In active/active mode, all the machines in the cluster actively handle user requests sent by an external load balancer. The load balancer hosts the cluster VIP and routes user requests to a device defined in its cluster group based on source-IP routing. If a device goes offline, the load balancer adjusts the load on the other active device.
In a well-connected campus network, where the connectivity is more LAN-like than WAN-like, the Ivanti Connect Secure can be clustered in separate buildings.
Customizing the Interface to Match a Company's Look-and-Feel
Ivanti Connect Secure enables you to customize a variety of elements in the end-user interface.
You can use the customization features to:
•Update the look-and-feel of the ICS's end-user console, so it will resemble one of your company's standard web pages or applications.
•Modify the headers, background colors, and logos that display in the sign-in page and end-user console to match your company's style.
•Order the bookmark display at the end user help system.
•Display the end-user home page to users (either in standard or customized form), and then choose to redirect users to a different page (such as your company's Intranet) when users first sign into the ICS console. On choosing to use this option, you may want to add links to your ICS's bookmarks on the new page.
•Configure custom sign-in pages through the ICS's admin console. The custom sign-in pages feature does not limit the number of customizations you can make to your pages. Using this feature, you can use an HTML editor to develop a sign-in page that exactly matches your specifications.
Supporting Users on Different Devices to Access Ivanti Connect Secure
Ivanti Connect Secure is accessed from standard workstations and kiosks running on Windows, Mac OSX, and Linux operating systems. End users can also access the ICS from connected Smart Phones and Tablets.
When a user connects from a Smart Phone or a Tablet, the ICS determines which pages and functionality to display based on settings that you configure.
For more information about specifying which pages get displayed on different devices, see the Ivanti Connect Secure Supported Platform Guide.
Providing Secure Access for International Users
Ivanti Connect Secure supports localization to include English (US), French, German, Spanish, Simplified Chinese, Traditional Chinese, Japanese, and Korean. When users sign into the device, it automatically detects the correct language to display based on the web browser setting. Alternatively, you can use end-user localization and custom sign-in page options to manually specify the language that you want to display to your end users.
Configuring Ivanti Connect Secure
The following basic steps need to be completed to enable users to start using Ivanti Connect Secure.
1.Plug in the Ivanti Connect Secure device and connect it to your network. Configure the initial system and network settings (see the PSA Series Hardware Guide for more information).
2.When you first sign into the admin console, an initial configuration task guide display, to walk you through the upgrade and installation of product licenses process. To view the configuration task guide, click Guidance in the upper right corner of the admin console.
3.Set the system date and time, upgrade to the latest service package, and install your product licenses.
4.Followed by the installation of product licenses, use the following steps to set up your access management framework to enable users to authenticate and access resources.
Create a test scenario to familiarize yourself with the process (see Creating a Test Scenario to Learn Concepts and Best Practices for more information).
5.Define an authentication server that verifies user names and passwords.
6.Create the user roles that enable access mechanisms, session options, and UI options for user groups.
7.Create a user authentication realm that specifies the conditions that users must meet to sign into the device.
8.Define a sign-in policy that specifies the URL that users must access to sign into the device and the page that they see when they sign in.
9.Create resource profiles that control access to resources, specify which user roles can access them, and include bookmarks that link to the resources.
After completing the basic steps, your system is ready for use. You can start using it as it is or configure additional advanced features such as endpoint defense and clustering.
Introducing the Ivanti Secure Access Client
The Ivanti Connect Secure gateway is the server component of a larger client-server solution. Ivanti allows many different clients to provide an array of secure-connectivity services to end users.
Ivanti Secure Access Client for Desktop
Ivanti Secure Access Client for desktop clients are fully-featured secure-connectivity clients that can be deployed either directly from the Ivanti Connect Secure gateway or via other third-party software distribution mechanisms (e.g., SMS). The Ivanti Secure Access Client support Windows and Mac OSX.
The Windows desktop client provides VPN, Host Checker, and Layer-2 (NAC) functionality, whereas the OSX desktop client provides VPN and Host Checker functionality. The Ivanti Secure Access Client can be downloaded from https://forums.ivanti.com/s/product-downloads?language=en_US without having to download the Ivanti Connect Secure gateway packages. Refer to the Ivanti Secure Access Client documentation for detail.
Ivanti Secure Access Client for Mobile
Ivanti Secure Access Client for mobile is made available through App Stores (rather than hosted on the Ivanti Connect Secure gateway). Ivanti offers mobile clients for iOS, Android, Google Chrome OS.
Ivanti Secure Access Client is designed to be lightweight and work tightly within the "sandboxes" provided by the mobile operating systems. The exact functionality of each mobile client varies according to the operating system, so, refer to the Ivanti Secure Access Client documentation for details on the capability of each mobile client.
Integrated Clients
There are many clients that are integrated directly into the Ivanti Connect Secure gateway. They are deployed by the ICS gateway and cannot be acquired independently from the ICS gateway. For the most part, these integrated clients are accessed by end users via a web browser connected to the ICS gateway.
.