FIPS Level 1 Support (Software FIPS)
Understanding Ivanti FIPS Level 1 Support
What Is FIPS?
Federal Information Processing Standard (FIPS) are a set of standards that define security requirements for products that implement cryptographic modules used to secure sensitive but unclassified information. The most recent standards are defined in the FIPS Publication 140-2.
The FIPS documents define, among other things, security levels for computer and networking equipment. U.S. Federal Government departments, and other organizations, use FIPS to evaluate the cryptographic capabilities of the equipment they consider for purchase. Cryptographic modules are validated against separate areas of the FIPS specification. An overall certification level is assigned based on the minimum level achieved in any area. Although primarily aimed at environments requiring strict security, FIPS levels are increasingly enforced as qualifying criteria for all U.S. Federal Government contracts. Security-conscious private enterprises might also use FIPS levels as an equipment evaluation benchmark. FIPS levels also serve as a customer-neutral description of vendor requirements. Vendors can engineer security products to FIPS levels and extend the applicability and eligibility of these products across a broad customer base, thereby eliminating exhaustive and time-consuming customer-by-customer product qualification procedures.
What Is FIPS Level 1 Support?
Ivanti offers FIPS level 1 support for both Ivanti Connect Secure and Policy Secure. Both services use a 140-2 level 1 certified cryptographic module to comply with FIPS. When FIPS level 1 support is enabled applications, such as browsers, accessing the web server must support Transport Layer Security (TLS), the latest version of Secure Socket Layer (SSL). If the platform features hardware acceleration, then for SSL processing SSL hardware acceleration is disabled as hardware acceleration does not comply with FIPS validation. Only FIPS approved algorithms are used when in FIPS level 1 support is enabled.
For more information about the Cryptography Module, see the validation certificate. To see historical and revoked module lists, validated cryptographic modules
Enabling FIPS Level 1 Support
Once you enable FIPS level 1 support, your browser is restricted to specific custom cipher strengths. A list of supported ciphers is shown during the enabling process.
When you enable FIPS level 1 support, the following events occur on the system:
•The Web server restarts and turns on FIPS level 1 support. The Web server now allows only TLSv1.0, TLSv1.1 and TLSv1.2 protocols that include FIPS approved cryptographic algorithms which include Suite B cipher suites.
Once FIPS level 1 support is enabled, new client sessions will use FIPS if the client supports FIPS. Existing client sessions may not be using FIPS. To ensure FIPS capable clients are in FIPS level 1 support, all client sessions should be terminated after the FIPS level 1 support is enabled. Administrators can use the System > Status > Active Users page to terminate client sessions.
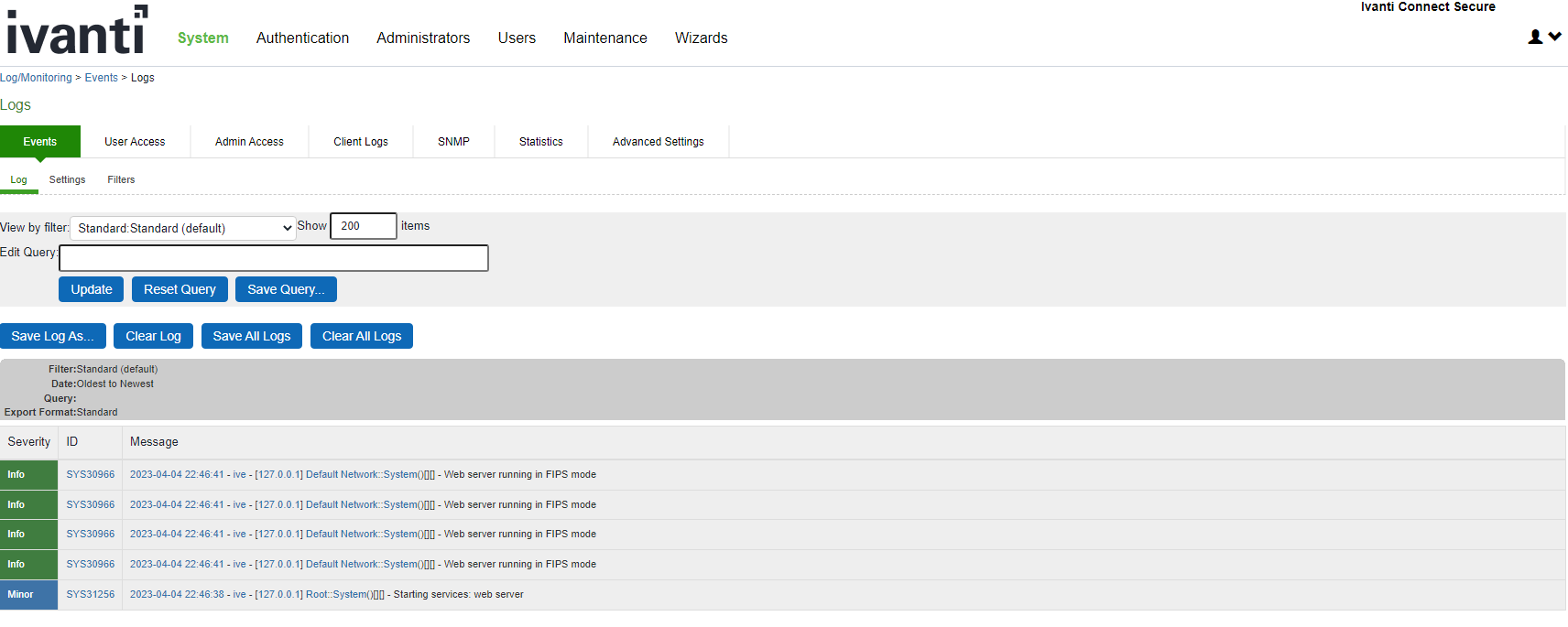
The following event logs are generated for FIPS level 1 support:
•SYS30966 when the web server turns FIPS level 1 support on.
•ADM30965 when the administrator turns FIPS level 1 support on or off.
•ERR30967 when the web server fails to turn on FIPS level 1 support.
To enable FIPS level 1 support:
1.Select System > Configuration > Security > Inbound SSL Options.
Under SSL FIPS Mode option, select Turn on FIPS mode. See Enabling FIPS Level 1 Support
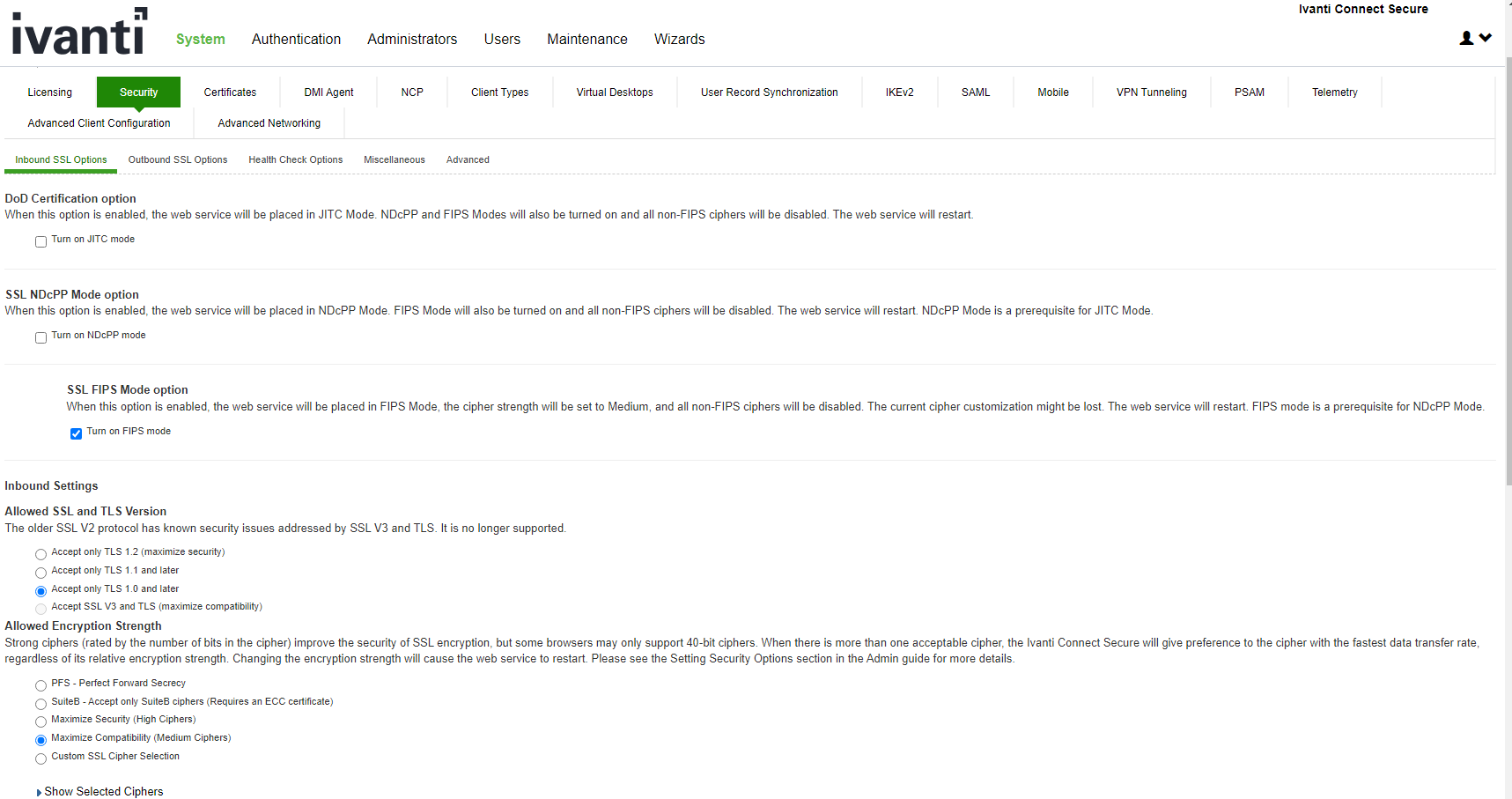
Once you turn on FIPS level 1 support, the following changes are made:
•Under Allowed SSL and TLS Version, the Accept only TLS 1.0 and later option is selected.
•Under Allowed Encryption Strength, the Maximum Compatibility Ciphers is set. See Enabling FIPS Level 1 Support Only FIPS approved algorithms are selected. All other options under this section are disabled. See Supported Cipher Suites when FIPS Level 1 Support is Enabled
•Under Encryption Strength, the Do not allow connections from browsers that only accept weaker ciphers option is selected. You cannot disable this selection.
2.Click Save Changes.
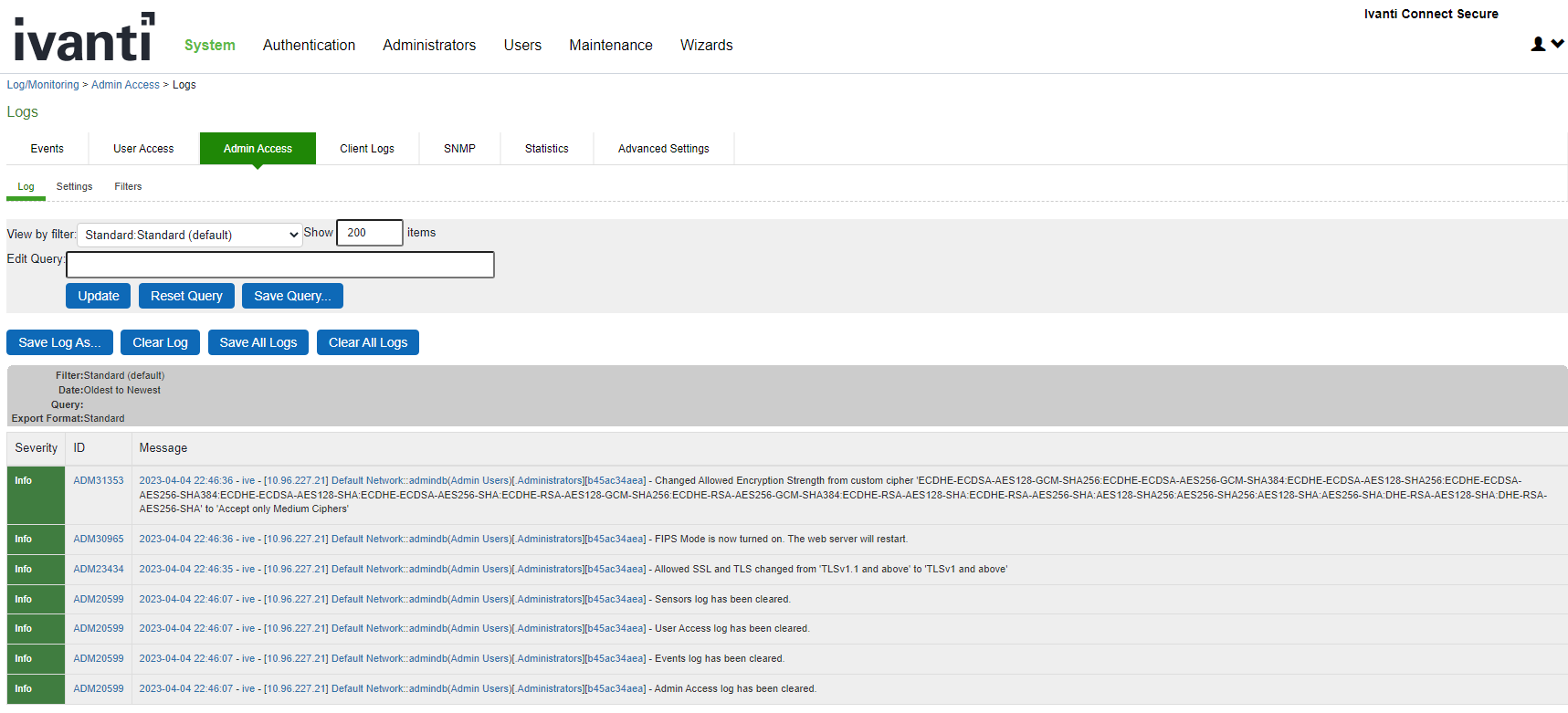
3.Entries are made in the Events logs (see Events Log Entries for FIPS Level 1) and Admin Access logs (see Admin Access Logs for FIPS Level 1 Encryption Strength Changes) to show that FIPS level 1 support is enabled.
Events Log Entries for FIPS Level 1
Admin Access Logs for FIPS Level 1 Encryption Strength Changes
Turning Off FIPS Level 1 Support from the Serial Console
|
Problem |
Description: If you have FIPS level 1 support enabled and your browser does not support the required cipher suites, you cannot access the device. If this happens to an administrator account, you can no longer administer or configure the system. |
|
Solution |
You can turn off FIPS level 1 support and reset the encryption strength from the device's serial console. After choosing that option, SSL options are reset to Accept only TLS 1.0 and later and to Maximum Compatibility (Medium Ciphers). Open a serial console to your device and select option 8. Turn off FIPS Mode and reset allowed encryption strength for SSL. |
Turning Off FIPS Level 1 and Resetting Encryption Strength from the Serial Console
Please choose the operation to perform:
1.Network Settings and Tools
2.Create admin username and password
3.Display log/status
4.System Operations
5.Toggle password protection for the console (Off)
6.Create a Super Admin session.
7.System Maintenance
8.Turn off FIPS Mode and reset allowed encryption strength for SSL
Choice: 8
Once you turn off FIPS level 1 support, option 8 is relabeled "Reset allowed encryption strength for SSL."
Installing a Self-Signed Certificate from the Serial Console
|
Problem |
Description: An administrator can be locked out of the system if their browser does not support the certificate assigned to the network port. For example, if your system has an ECC certificate assigned to the internal port and your browser does not support ECC certificates you cannot log in to the device using the internal port. |
|
Solution |
You can use the serial console to create and install a self-signed RSA certificate onto the internal port to allow access. Once you connect to the serial console, select option 4. System Operations followed by Option 7. Install self-signed certificate. It may take a few minutes for the 2048-bit key size self-signed certificate to be created and installed on your device. Once the certificate is installed, you can now log in to the device. |
Creating and Installing an RSA Certificate from the Serial Console
Please choose the operation to perform:
1.Network Settings and Tools
2.Create admin username and password
3.Display log/status
4.System Operations
5.Toggle password protection for the console (Off)
6.Create a Super Admin session.
7.System Maintenance
8.Turn off FIPS Mode and reset allowed encryption strength for SSL
Choice: 4
Please choose the operation to perform:
1.Reboot this Ivanti Connect Secure
2.Shutdown this Ivanti Connect Secure
3.Restart services at this Ivanti Connect Secure
4.Rollback this Ivanti Connect Secure
5.Factory reset this Ivanti Connect Secure
6.Clear all configuration data at this Ivanti Connect Secure
7.Install self-signed certificate
Choice: 7
Are you sure you want to install a newly-created RSA self-signed certificate on the internal port? (y/n) y
Please provide information to create a self-signed Web server
digital certificate.
Common name (example: secure.company.com): myname.mycompany.com
Organization name (example: Company Inc.): MyCompany Inc.
Please enter some random characters to augment the system's
random key generator. We recommend that you enter approximately
thirty characters.
Random text (hit enter when done):abcdef1234567
Creating self-signed digital certificate - this may take several minutes...
The self-signed digital certificate was successfully created.
Supported Cipher Suites when FIPS Level 1 Support is Enabled
The tables in this topic list the cipher suites that are supported by the web server when the FIPS level 1 support is enabled.
When FIPS level 1 support is enabled, only TLSv1.0, v1.1, v1.2 and AES256, 3DES and AES128 are allowed. The order of the cipher suites is not dependent on the SSL hardware acceleration module since hardware acceleration is not used when FIPS level 1 support is enabled.
When FIPS level 1 support is enabled, the following settings are automatically configured:
•In the SSL Options window:
•Under Allowed SSL and TLS Version, the Accept only TLS 1.0 and later option is selected. All other options under this section are disabled.
•Under Allowed Encryption Strength, the Maximum Compatibility ciphers option is selected. Only FIPS approved algorithms are selected. All other options under this section are disabled.
•Under Encryption Strength Option, the Do not allow connections from browsers that only accept weaker ciphers option is selected.
•SSL hardware acceleration is disabled. IPsec hardware acceleration is not affected by the FIPS level 1 support being enabled.
In the following table, the first four cipher suites are given preference due to the requirements in RFC 6460. The first two cipher suites meeting the requirement for Suite B Profile for TLS 1.2. The next two meeting the requirement for Suite B Transitional Profile for TLS 1.0 and 1.1.
The following table lists the Supported Cipher Suites with FIPS Level 1 Support on and ECC Server Certificates in Use:
|
Cipher Suite |
Protocol |
|
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 |
TLSv1.2 |
|
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 |
TLSv1.2 |
|
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 |
TLSv1.2 |
|
TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384 |
TLSv1.2 |
|
TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384 |
TLSv1.2 |
|
TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384 |
TLSv1.2 |
|
TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384 |
TLSv1.2 |
|
TLS_ECDH_RSA_WITH_AES_256_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 |
TLSv1.2 |
|
TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256 |
TLSv1.2 |
|
TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256 |
TLSv1.2 |
|
TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256 |
TLSv1.2 |
|
TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256 |
TLSv1.2 |
|
TLS_ECDH_RSA_WITH_AES_128_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA |
TLSv1.0 and later |
The following table lists the Supported Cipher Suites with FIPS Level 1 Support on and RSA Server Certificates in Use:
|
Cipher Suite |
Protocol |
|
TLS_RSA_WITH_AES_256_CBC_SHA256 |
TLSv1.2 |
|
TLS_RSA_WITH_AES_256_CBC_SHA |
TLSv1.0 and later |
|
TLS_RSA_WITH_3DES_EDE_CBC_SHA |
TLSv1.0 and later |
|
TLS_RSA_WITH_AES_128_CBC_SHA256 |
TLSv1.2 |
|
TLS_RSA_WITH_AES_128_CBC_SHA |
TLSv1.0 and later |
|
TLS_RSA_WITH_AES_256_GCM_SHA384 |
TLSv1.2 |
|
TLS_RSA_WITH_AES_128_GCM_SHA256 |
TLSv1.2 |
|
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 |
TLSv1.2 |
|
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 |
TLSv1.2 |
|
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA |
TLSv1.0 and later |
|
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 |
TLSv1.2 |
|
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 |
TLSv1.2 |